In the vast landscape of cyber security, one term that has gained prominence is “whaling attacks.” If you’ve ever wondered what these attacks entail, you’re in the right place. Whaling attacks refer to a type of cyber threat where high-profile individuals, such as CEOs or senior executives, become the target. With a focus on extracting sensitive information or tricking individuals into wire transfers, these attacks can have severe consequences. This article aims to shed light on the intricacies of whaling attacks, helping you navigate the evolving world of cyber security with confidence.
Definition of Whaling in Cyber Security
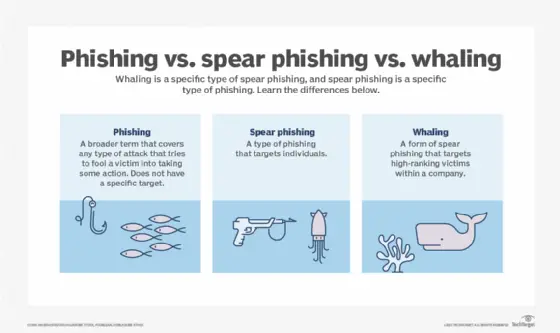
Basics of whaling
Whaling, in the context of cyber security, refers to a highly targeted and sophisticated type of cyber attack that focuses specifically on high-profile individuals or organizations. Unlike phishing attacks that cast a wide net hoping to catch unsuspecting victims, whaling attacks are carefully crafted to deceive and exploit their targets. This form of cyber attack is named after the hunting technique of hunting whales, as it aims to single out and capture valuable prey.
Differentiating whaling from other cyber threats
While whaling attacks may share some similarities with other forms of cyber threats, there are distinct characteristics that differentiate them. One key aspect is the level of specificity and personalization involved in whaling attacks. These attacks often involve extensive reconnaissance to gather information about the target, enabling the attacker to tailor their approach to appear legitimate and trustworthy.
Another differentiating factor is the scale of the target. Whaling attacks typically focus on high-ranking executives, government officials, or individuals with access to sensitive information or valuable assets. By targeting individuals or entities of significance, the potential rewards for the attacker are significant, whether it be financial gain or acquiring confidential data.
Significance of understanding whaling
Understanding whaling attacks is crucial in today’s cyber landscape. As these attacks become increasingly prevalent and sophisticated, organizations and individuals need to be aware of the risks they pose and the measures they can take to protect themselves. By comprehending the unique characteristics and protocols of whaling attacks, individuals can strengthen their defenses and minimize the potential impact of such attacks.
Characteristics of Whaling Attacks
Targeted individuals or entities
Whaling attacks specifically target individuals or entities with high-profile positions or access to valuable information. These targets are carefully selected based on their potential value to the attacker, such as CEOs, CFOs, or senior government officials. By focusing on high-ranking individuals, whaling attackers aim to exploit their authority or access privileges to gain unauthorized access or deceive others within the organization.
Sophistication of scams
Whaling attacks are known for their high level of sophistication. Attackers invest significant time and effort in conducting thorough research on their targets, allowing them to create convincing and personalized scams. These scams may involve impersonating trusted colleagues, clients, or even business partners, making it difficult for the targeted individual to identify the fraudulent nature of the communication or request.
Potential damage from attacks
The potential damage caused by whaling attacks can be severe. If successful, attackers can gain access to sensitive information, financial resources, or even compromise the network infrastructure of an organization. This can lead to financial losses, reputational damage, and potential legal implications. Additionally, whaling attacks can also result in the loss of customer trust and confidence, further impacting the affected entity’s business operations.
Protocols of a Whaling Attack

Phishing emails
Phishing emails are a common method used in whaling attacks. Attackers craft emails that appear legitimate, often using social engineering techniques to deceive the target into taking a specific action. These emails may contain malicious attachments or links that, when clicked, lead to the compromise of sensitive information or the installation of malware.
Website/URL manipulation
Whaling attackers may manipulate websites or URLs to further deceive their targets. This could involve creating fake login pages that resemble legitimate ones, tricking the target into providing their credentials or personal information. By manipulating websites or URLs, attackers can make their scams appear more convincing, increasing the likelihood of a successful attack.
Data and identity theft
Whaling attacks often involve the theft of both data and identity. Attackers aim to gain unauthorized access to sensitive information, such as financial records, intellectual property, or personally identifiable information. With this stolen data, attackers can exploit it for financial gain, commit fraud, or sell it on the dark web. The theft of identities can also be used for further phishing attempts or other malicious activities.
Notable Whaling Attacks in History
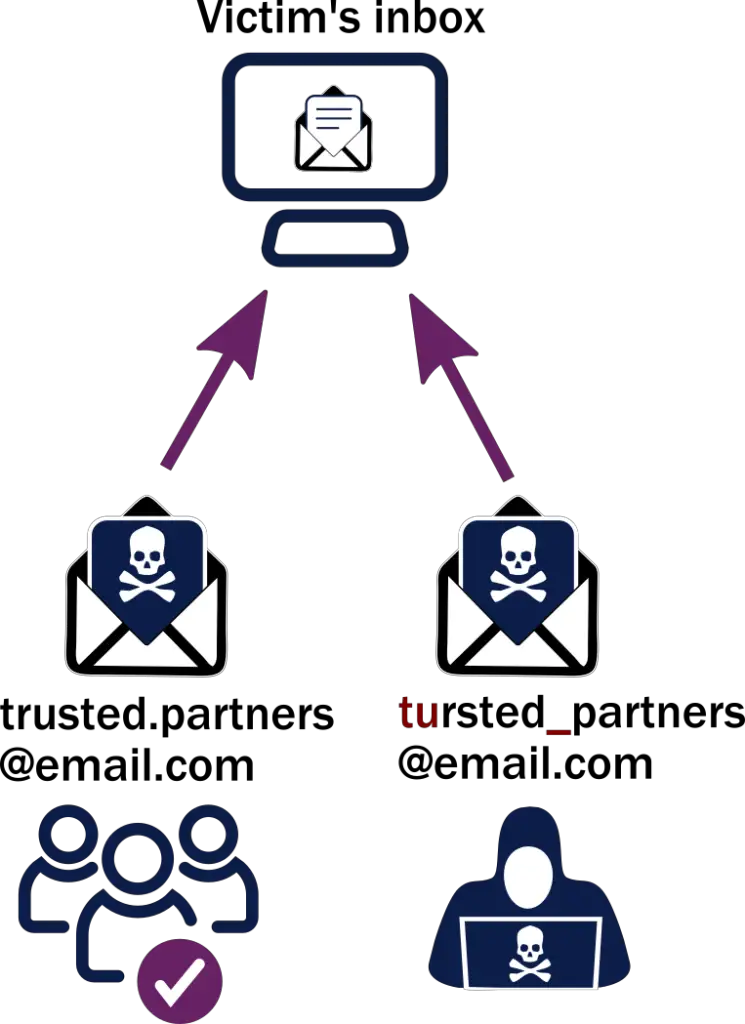
The FBI whaling attack
In 2016, a whaling attack targeted the Chief Financial Officer (CFO) of the investment firm Ubiquiti Networks. The attacker impersonated an employee from the company’s external legal counsel, requesting a transfer of $46.7 million to a designated account. The attack succeeded, resulting in substantial financial losses for Ubiquiti Networks.
The Snapchat payroll incident
In 2016, Snapchat fell victim to a whaling attack that compromised employee payroll information. The attacker masqueraded as the CEO and requested a payroll department employee to send confidential employee data. The incident resulted in a temporary setback for Snapchat as they faced reputational damage and had to strengthen their cyber security measures.
Ubiquiti Networks financial loss
In 2015, Ubiquiti Networks, an American technology company, fell victim to a whaling attack that resulted in a significant financial loss. Attackers targeted the company’s finance department using spoofed emails, convincing employees to transfer funds to an unknown bank account. The attack highlighted the vulnerabilities that high-profile organizations can face and the importance of implementing robust security measures.
How Whaling Attacks Endanger Businesses
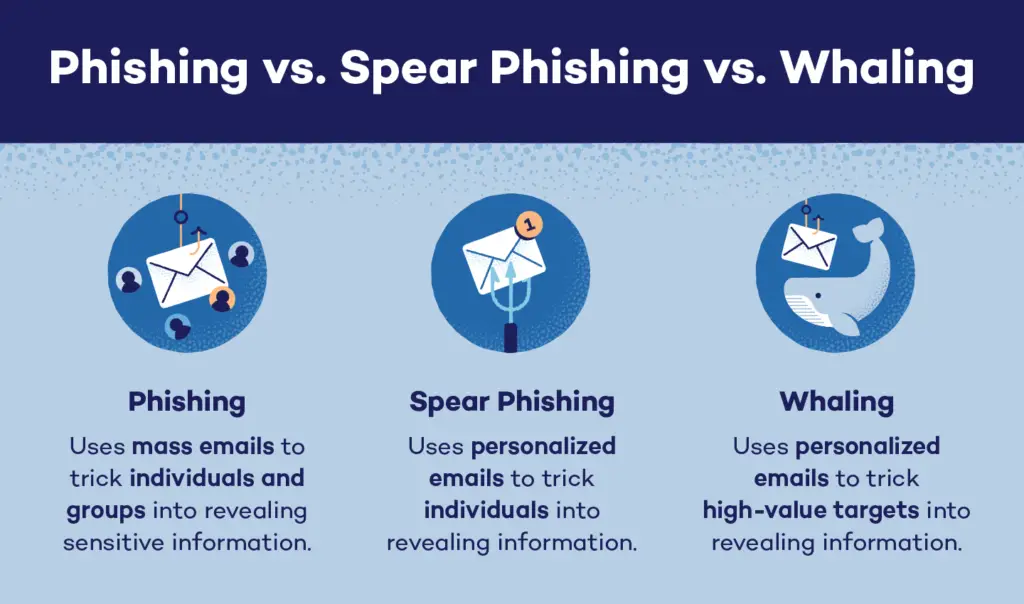
Financial loss
Whaling attacks can have severe financial consequences for businesses. By bypassing traditional security measures and exploiting the authority of targeted individuals, attackers can orchestrate fraudulent transactions or transfers, resulting in substantial monetary losses. These financial losses can disrupt operations, hinder growth, and even lead to bankruptcy in extreme cases.
Data breach consequences
When successful, whaling attacks can lead to significant data breaches. Attackers gain access to sensitive information, such as customer data, financial records, or intellectual property, which can have serious legal and reputational consequences. Data breaches can result in regulatory penalties, lawsuits, loss of customer trust, and damage to a company’s reputation in the marketplace.
Damage to enterprise reputation
Whaling attacks can have a detrimental impact on an enterprise’s reputation. Once news of a successful attack emerges, customers, partners, and stakeholders may lose confidence in the affected organization’s ability to secure their data and protect their interests. A damaged reputation can be difficult to recover, leading to lost business opportunities and a decreased market value for the affected entity.
Whaling Attacks and Personal Security
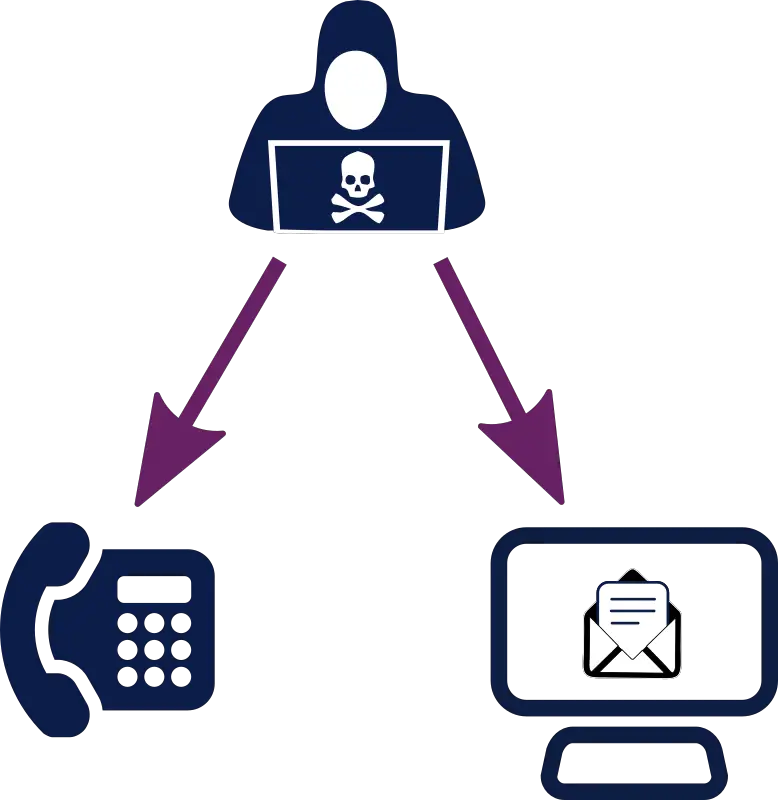
Identity theft risks
Whaling attacks pose significant risks to personal security, particularly through identity theft. Attackers who gain access to personal information can use it to impersonate individuals, commit financial crimes, or gain unauthorized access to various accounts. The repercussions of identity theft can be long-lasting, with victims facing financial and emotional burdens in attempting to recover from such attacks.
Financial scams
Whaling attacks often involve sophisticated financial scams that target individuals’ personal finances. Attackers may use phishing emails or fraudulent websites to trick individuals into providing their banking credentials or credit card information. Once obtained, this data can be used for fraudulent transactions, making the individual vulnerable to financial loss and fraudulent activity.
Privacy breaches
A successful whaling attack puts an individual’s privacy at risk. Attackers may gain access to personal emails, messages, or confidential documents, which can be used to blackmail or manipulate individuals. Furthermore, personal information obtained through these attacks can be sold on the dark web, perpetuating further privacy breaches and illegal activities.
Methods Used in Whaling Attack Detection
Email anomaly detection
Email anomaly detection systems play a crucial role in identifying potential whaling attacks. These systems analyze email metadata, content, and the sending patterns of a user to identify suspicious or abnormal behavior. By flagging potentially fraudulent emails or phishing attempts, these systems can help organizations and individuals stay vigilant and take necessary precautions.
Website security measures
Ensuring robust website security is essential in combating whaling attacks. Implementations such as secure socket layer (SSL) certificates, secure coding practices, and regular vulnerability scans can help protect against URL manipulation and phishing attempts. Additionally, web application firewalls and intrusion detection systems can detect and block unauthorized access attempts, reducing the risk posed by potential whaling attacks.
End-user education
Educating end-users and employees about whaling attacks is crucial in detection and prevention. By providing training on recognizing suspicious emails, verifying sources, and adhering to secure communication practices, individuals can better protect themselves and their organizations from falling victim to whaling attacks. Regular awareness campaigns and simulated phishing exercises can help reinforce good security habits and raise overall cyber security awareness within an organization.
Best Practices to Prevent Whaling Attacks
Implementing multifactor authentication
Implementing multifactor authentication (MFA) adds an extra layer of security and minimizes the risk of unauthorized access. By requiring users to provide multiple forms of verification, such as a password, a unique code sent to their phone, or a biometric identifier, the likelihood of a successful whaling attack is reduced. MFA serves as a valuable defense mechanism against attackers attempting to exploit user credentials.
Regularly updating security software
Keeping security software up to date is essential in preventing whaling attacks. Regularly patching and updating operating systems, antivirus software, and firewalls ensures that known vulnerabilities are addressed before attackers can exploit them. Additionally, updating software reduces the likelihood of falling victim to socially engineered attacks, as software vendors often release security patches in response to emerging threats.
Employee cybersecurity training
Instituting comprehensive employee cybersecurity training programs is vital in preventing whaling attacks. Training should cover topics such as identifying suspicious emails, verifying sources, and reporting potential security incidents. By empowering employees with the knowledge and skills to detect and respond appropriately to whaling attacks, organizations can reduce the risk of successful attacks and strengthen their overall security posture.
How to React to a Potential Whaling Attack
Verifying the source
When faced with a potential whaling attack, it’s essential to verify the source of the communication. By independently confirming the legitimacy of the sender, such as through a phone call or face-to-face conversation, individuals can ensure they are not falling victim to a fraudulent request. Avoid relying solely on the content of the communication or any included links or attachments when verifying the authenticity.
Notify IT security team
If you suspect a whaling attack, it is crucial to immediately notify your organization’s IT security team. They are equipped to handle such incidents, investigate the situation, and take appropriate measures to mitigate the potential damage. Reporting the incident promptly allows the IT team to take swift action and implement safeguards to protect other individuals or entities within the organization.
Disseminate information to warn others
Once you have confirmed a whaling attack or suspicious activity, it is imperative to disseminate this information within your organization. By informing colleagues, superiors, and relevant departments, you can help raise awareness and prevent others from falling victim to similar attacks. Promptly sharing detailed information about the attack can empower others to remain vigilant and take necessary precautions to protect themselves and the organization.
Future of Whaling Attacks in Cyber Security
Predicted growth of whaling attacks
As technology continues to advance and cyber attackers become more sophisticated, the prevalence of whaling attacks is expected to increase. The potential rewards for attackers targeting high-profile individuals or entities make whaling attacks an attractive option. Organizations and individuals alike must remain proactive in their security efforts to stay ahead of these evolving threats.
Evolving measures to combat attacks
As whaling attacks evolve, so do the measures used to combat them. Cyber security professionals and researchers continually develop new tools and techniques to detect, prevent, and mitigate the risks posed by these attacks. Advancements in artificial intelligence, machine learning, and threat intelligence will play a vital role in enhancing security protocols and identifying potential whaling attacks before they can cause significant damage.
Impact of technological advancements on whaling threats
The rapid advancement of technology presents both opportunities and challenges in combating whaling attacks. While technological innovations can improve security measures, they can also be leveraged by attackers to launch more sophisticated attacks. As technologies such as artificial intelligence, internet of things, and cloud computing continue to shape the digital landscape, organizations and individuals must adapt their security strategies accordingly to protect against whaling threats.
In conclusion, whaling attacks pose a significant risk to both individuals and organizations. The increasing sophistication and personalized nature of these attacks require heightened awareness and proactive security measures. By understanding the characteristics, protocols, and consequences of whaling attacks, individuals and organizations can better protect themselves from falling victim to these targeted cyber threats. As the cyber threat landscape continues to evolve, remaining vigilant and adopting best practices will be key in effectively combating whaling attacks and safeguarding sensitive information.


“Whaling attacks are just like deep-sea fishing, but for hackers. Scary, huh?”
“Whaling attacks are so sneaky, they might as well be swimming with actual whales 🐋🐠 #cybersecurity”
“Whaling in cyber security? I thought it was some kind of fishing technique. Mind blown!”
Actually, whaling in cyber security refers to a specific type of phishing attack targeting high-profile individuals or organizations. It’s important to stay informed and not jump to conclusions. Keep your mind open, buddy!
“Whaling attacks? Sounds fishy, but we better understand ’em before they harpoon us!”
“Whaling attacks are like a twisted version of Moby Dick in the cyber world. Scary stuff!”
I never knew cyber criminals were so into marine life! Whaling attacks, seriously? 🐋🤷♀️
“Whaling attacks sound like something straight out of a spy movie! Cybersecurity is evolving, folks!”