In the world of cyber security, non-repudiation plays a crucial role in ensuring the integrity and accountability of digital transactions. This concept refers to the ability to verify the source and authenticity of a message or action, preventing individuals from denying their involvement in a particular activity. By establishing a reliable system of non-repudiation, organizations can safeguard against fraud, disputes, and unauthorized access, ultimately bolstering trust and confidence in online interactions. In this article, we will explore the importance of non repudiation in cyber security and delve into its various applications and benefits. So, let’s unravel the mysteries behind non-repudiation and discover how it safeguards the digital realm!
Definition of Non-Repudiation in Cyber Security
Explaining the concept of non-repudiation
Non-repudiation is a critical concept in the realm of cybersecurity. It refers to the ability to prove the authenticity and integrity of transactions or communications, ensuring that the parties involved cannot deny their involvement or the actions they have taken. In other words, it provides irrefutable evidence that a particular action was performed by a specific party, and that the action cannot be denied or refuted.
Differentiating between repudiation and non-repudiation
To understand non-repudiation, it is important to differentiate it from repudiation. Repudiation refers to the act of denying one’s involvement or the actions they have taken. In the context of cybersecurity, repudiation can present a significant challenge as it allows malicious actors to deny their responsibility for unauthorized activities. Non-repudiation, on the other hand, ensures that such denials are not possible by providing strong evidence and proof of the actions taken.
Significance of non-repudiation in the realm of cyber security
Non-repudiation plays a crucial role in ensuring the security and integrity of digital transactions and communications. By providing undeniable evidence of actions and transactions, it enables organizations and individuals to hold accountable those who engage in malicious activities or attempt to deny their involvement. Non-repudiation also helps establish trust and confidence in digital systems, as it provides assurance that the parties involved are who they claim to be and that the actions they have taken are genuine and verifiable.
The Role of Non Repudiation in Data Security
Mitigating the risk of data tampering
Data tampering is a significant concern in today’s digital landscape. Malicious actors may attempt to modify or manipulate data to suit their interests, compromise the integrity of information, or deceive others. Non repudiation ensures that data cannot be tampered with without leaving a trace, as any alteration or modification would be detectable and attributed to the responsible party. This serves as a deterrent to potential data tampering, as well as enabling swift identification and response to any such incidents.
Ensuring accountability and responsibility
Non repudiation establishes a strong sense of accountability and responsibility in digital transactions and interactions. With the capability to prove the origin and authenticity of actions, it becomes significantly harder for individuals or organizations to deny their involvement or shift blame onto others. This not only facilitates fair and just resolution of disputes but also acts as a deterrent against fraudulent or malicious activities.
Non repudiation also plays a crucial role in safeguarding against unauthorized data access. By providing strong evidence of the parties involved in accessing or manipulating data, it becomes easier to identify and respond to any unauthorized access attempts or breaches. This helps in protecting sensitive information, maintaining the confidentiality of data, and preventing unauthorized individuals from gaining unauthorized access.
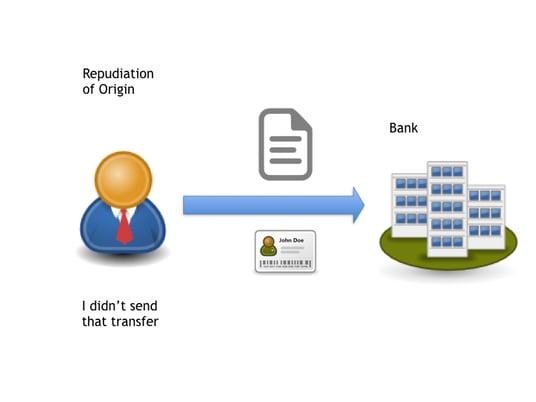
Non-Repudiation and Cyber Threats
Types of threats that non-repudiation can mitigate
Non-repudiation serves as a powerful tool in mitigating various cyber threats. It helps counter attacks such as identity theft, where malicious actors attempt to impersonate legitimate users and deny their involvement. It also addresses instances of unauthorized data modification or deletion where the responsible party attempts to evade responsibility. By ensuring that the evidence of actions cannot be refuted, non-repudiation provides strong protection against these threats.
Role in countering cyber attacks
In the face of evolving and sophisticated cyber attacks, non-repudiation plays a vital role in countering these threats. It allows for the identification and attribution of malicious activities, enabling prompt responses and mitigating the damage caused. Non-repudiation ensures that attackers cannot deny their involvement or claim innocence, providing solid evidence for legal proceedings or remedial actions.
Non-repudiation’s influence in reducing cyber fraud
Cyber fraud is a significant concern for individuals and organizations. Non-repudiation serves as a robust defense against fraud by providing undeniable evidence of transactions and interactions. It makes it extremely difficult for fraudsters to deny their involvement or claim innocence, acting as a deterrent and discouraging fraudulent activities. This not only protects individuals and businesses from financial losses but also helps in building trust in digital transactions and systems.
Key Components of Non-Repudiation
Access control
Access control is a fundamental component of non-repudiation. It involves implementing mechanisms to regulate and control the access to sensitive information and resources. By enforcing strict access control policies, organizations can ensure that only authorized individuals have access to critical systems and data. This helps in establishing a reliable audit trail and attributing actions to specific users.
Identity verification
Identity verification plays a crucial role in non-repudiation. It involves verifying the identity of individuals involved in transactions or interactions to ensure their authenticity. Methods such as multi-factor authentication, biometrics, and digital certificates are commonly used for identity verification. By confirming the identity of users, organizations can establish a strong foundation for non-repudiation and prevent unauthorized individuals from engaging in malicious activities.
Digital signatures
Digital signatures provide a mechanism for authenticating and ensuring the integrity of electronic documents and messages. They are used to verify the identity of the sender and guarantee the integrity of the content. Digital signatures are based on asymmetric encryption algorithms, where the sender uses their private key to encrypt the document, and the recipient uses the sender’s public key to verify the signature. Digital signatures play a vital role in non-repudiation by providing strong evidence of the sender’s identity and integrity of the message.
Encryption
Encryption is another essential component of non-repudiation. It involves the conversion of information into a coded form to prevent unauthorized access. By encrypting data, organizations can protect sensitive information from unauthorized disclosure or modification. Encryption also plays a role in non-repudiation by ensuring the confidentiality and integrity of data, and preventing unauthorized individuals from accessing or tampering with the information.
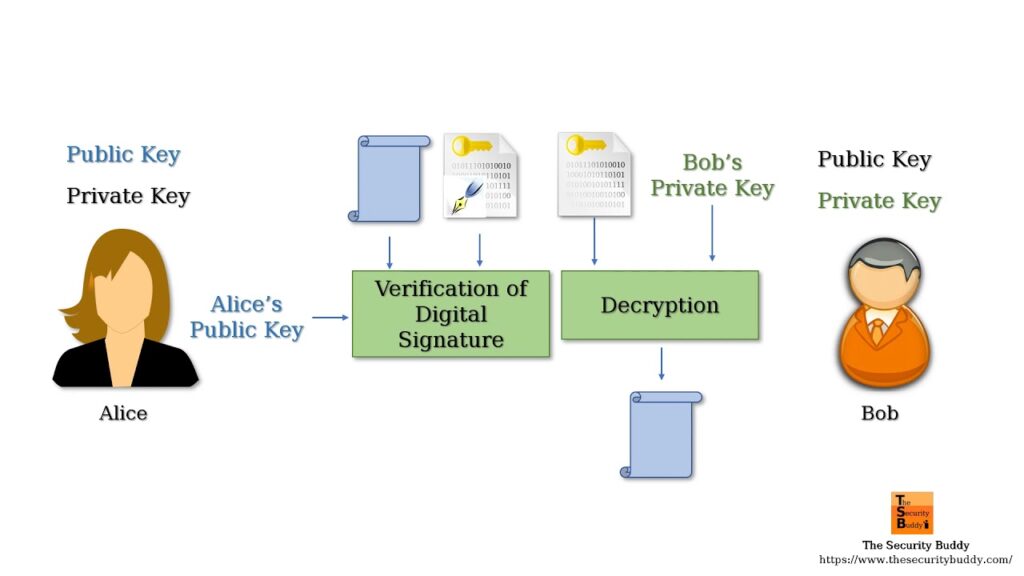
Techniques of Non-Repudiation in Cyber Security
Use of cryptographic techniques
Cryptographic techniques form the foundation of non-repudiation. These techniques include encryption, digital signatures, and hash functions, which are utilized to protect data, verify identities, and ensure the integrity of transactions. Cryptography ensures that information is secure, reliable, and tamper-proof, providing strong evidence for non-repudiation.
Employing digital signatures
Digital signatures are a widely used technique for non-repudiation. They involve the use of public key infrastructure (PKI) and asymmetric encryption algorithms to create a unique and verifiable signature. Digital signatures provide assurance that the document or message was not altered during transmission and that it originated from the claimed sender.
Usage of time stamps in non-repudiation
Incorporating timestamps in non-repudiation processes helps provide an accurate record of when a transaction or communication occurred. Time stamps serve as reliable evidence and ensure that actions cannot be denied by establishing a chronological order. By including timestamps, organizations can strengthen their non-repudiation mechanisms and enhance the integrity and verifiability of transactions.
Implementing hash functions
Hash functions play a crucial role in non-repudiation by generating a unique digital fingerprint or hash value for a message or document. This hash value is used to verify the integrity of the data and ensure that it has not been tampered with during transmission. Hash functions provide a quick and efficient way to verify the integrity of large volumes of data, making them an essential component of non-repudiation processes.
Non-Repudiation in Network Security
Function of non-repudiation in secure data transmission
Non-repudiation plays a significant role in ensuring the secure transmission of data across networks. By establishing the authenticity and integrity of data, it prevents malicious actors from tampering with or modifying information during transmission. Non-repudiation also acts as a deterrent against unauthorized data access, ensuring that only authorized parties can access and interact with network resources and data.
Protection of network from tampering and denial of service attacks
Networks are vulnerable to various types of attacks, such as tampering and denial of service (DoS) attacks. Non-repudiation helps protect networks by ensuring that any attempts to tamper with data or disrupt network services are detectable and attributable to the responsible parties. This enables swift identification and response to these attacks, minimizing their impact and ensuring the integrity and availability of network resources.
Promotion of trust within network communication
Trust is vital for effective network communication. Non-repudiation promotes trust by providing evidence of the authenticity and integrity of transactions and interactions. By establishing trust within network communication, organizations can confidently collaborate and share sensitive information, knowing that the actions of the parties involved cannot be denied or refuted.
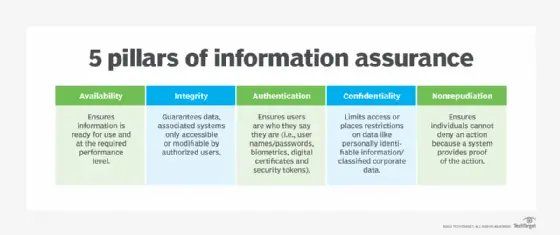
Limitations of Non-Repudiation in Cyber Security
Challenges in implementing non-repudiation
Implementing non-repudiation can present challenges for organizations. It requires the integration of various technologies, processes, and policies to ensure its effectiveness. Organizations may face technical difficulties in implementing robust cryptographic mechanisms or establishing secure key management practices. The complexity of non-repudiation can also lead to usability challenges for end-users, impacting its adoption and effectiveness.
Issue of key management and storage
Key management is a critical aspect of non-repudiation, as it involves the secure storage and distribution of cryptographic keys. Organizations must ensure the confidentiality and integrity of keys to prevent unauthorized access or misuse. Key management can be challenging, particularly for large-scale deployments, as it requires implementing secure key generation, distribution, storage, and revocation processes.
Potential vulnerabilities associated with non-repudiation
While non-repudiation is an essential component of cybersecurity, it is not without its vulnerabilities. Malicious actors may attempt to compromise the authenticity or integrity of non-repudiation mechanisms through various means, such as exploiting encryption weaknesses or compromising the integrity of key management processes. Organizations must be vigilant and continuously assess and update their non-repudiation systems to mitigate these vulnerabilities.
Non-Repudiation in Web Security
Importance in secure web transactions
Non-repudiation is crucial for securing web transactions, such as online banking or e-commerce. It ensures that the parties involved in the transaction cannot deny their involvement or the actions taken. By providing evidence of the transaction, including the identity of the participants and the integrity of the data, non-repudiation instills confidence and trust in web-based transactions.
Use in digital certificate validation
Digital certificates play a vital role in web security by facilitating secure communication and verifying the authenticity of websites. Non-repudiation is instrumental in validating digital certificates, ensuring that the certificates have not been tampered with and that they are issued by trusted authorities. By establishing non-repudiation, organizations can trust the information provided by digital certificates, safeguarding against phishing attacks and other web-based threats.
Role in preventing web-based hacking attempts
Web-based hacking attempts, such as SQL injection, cross-site scripting, or session hijacking, are pervasive threats in today’s digital landscape. Non-repudiation helps prevent these attacks by establishing the authenticity of web interactions and the integrity of data. By leveraging non-repudiation mechanisms, organizations can detect and respond to web-based hacking attempts promptly, minimizing the potential impact and damage caused.
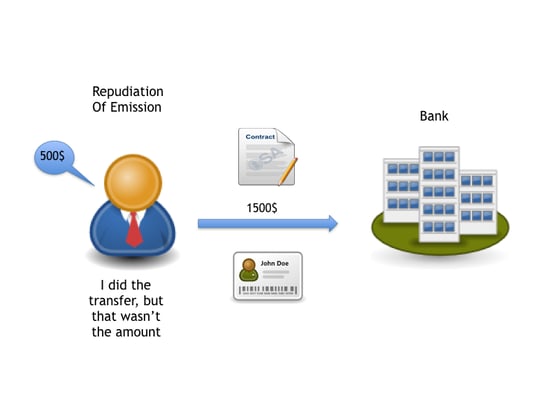
Non-Repudiation in Email Security
Role in establishing sender’s identity
Email remains a prevalent form of communication, making it susceptible to various threats, such as email spoofing or phishing attacks. Non-repudiation plays a critical role in establishing the identity of the email sender. By digitally signing emails, senders can provide proof of their identity, ensuring that the recipient can trust the authenticity of the email and verify its integrity.
Preventing email spoofing and phishing attacks
Email spoofing and phishing attacks are prevalent methods used by attackers to deceive individuals and gain unauthorized access to sensitive information. Non-repudiation helps prevent these attacks by enabling the recipient to verify the authenticity of the sender. By implementing strong non-repudiation measures, organizations can protect their employees and customers from falling victim to email-based scams and phishing attempts.
Use of digital signatures in emails
Digital signatures play a crucial role in email security by providing assurance of the sender’s identity and the integrity of the content. By digitally signing emails, senders can ensure that the email cannot be tampered with during transmission and that it originated from the claimed sender. This enhances non-repudiation in email communications, fostering trust and confidence in email exchanges.
Future of Non-Repudiation in Cyber Security
Non-repudiation in the era of quantum computing
The emergence of quantum computing poses challenges and opportunities for non-repudiation in cybersecurity. Quantum computing has the potential to compromise certain cryptographic algorithms currently used in non-repudiation. However, it also opens the door to new cryptographic techniques that can enhance the security and resilience of non-repudiation. The future of non-repudiation in the era of quantum computing will require the development and adoption of quantum-resistant algorithms to ensure the continued effectiveness of non-repudiation mechanisms.
Impact of non-repudiation on AI and machine learning
AI and machine learning technologies have the potential to enhance non-repudiation in cybersecurity. These technologies can be leveraged to analyze patterns and behaviors, detect anomalies, and identify potential threats or breaches. By integrating AI and machine learning algorithms into non-repudiation systems, organizations can strengthen their ability to detect and respond to attacks, reduce false positives, and enhance the overall security posture.
The role of non-repudiation in IoT security
The proliferation of Internet of Things (IoT) devices poses unique challenges to cybersecurity. Non-repudiation plays a crucial role in IoT security by ensuring the authenticity and integrity of data transmitted between IoT devices and systems. By implementing robust non-repudiation mechanisms, organizations can establish trust in IoT ecosystems, safeguard against unauthorized access or tampering, and enable secure and reliable interactions between devices.
In conclusion, non-repudiation is a fundamental concept in cybersecurity, providing strong evidence and assurance of the authenticity, integrity, and accountability of actions and transactions. From data security and mitigating cyber threats to web and email security, non-repudiation plays a vital role in ensuring trust, reducing fraud, and safeguarding digital systems. As technology continues to evolve, the future of non repudiation will require adapting to quantum computing, leveraging AI and machine learning, and addressing the unique challenges posed by the Internet of Things. By embracing and enhancing non-repudiation mechanisms, organizations can strengthen their cybersecurity defenses and build a more secure digital environment.

“Non-repudiation is like a superhero in the cyber world, saving us from liars and fraudsters! 🦸♂️ #NoMoreDenials”
Sorry to burst your bubble, but non-repudiation is no superhero. It’s just a security measure, not some magical power. And let’s be real, fraudsters will always find a way around it. #NotSoSuper #CyberReality
“Non-repudiation is like the ultimate ‘I told you so’ in cyber security! No backing out now!”
“Non-repudiation is like having an unbreakable alibi in the world of cyber security. No more finger-pointing!”
Oh please, like non-repudiation is foolproof. Cyber criminals always find a way to evade detection. Stop acting like it’s some kind of magic shield. It’s just another piece in the puzzle, my friend.
I never thought non-repudiation could be so cool! Cyber security just got interesting! 💻🔒
Non-repudiation is indeed a fascinating aspect of cyber security. It’s captivating how it ensures accountability and prevents individuals from denying their actions. It’s refreshing to see someone appreciate the intricacies of this field. Keep exploring and discovering more about the exciting world of cyber security! 💻🔒
Wow, non-repudiation sounds like a fancy term! But hey, isn’t it just common sense in cyber security?
Actually, non-repudiation is more than just common sense. It’s a crucial concept in cyber security that ensures accountability and prevents denial of actions. It’s important to understand these terms to fully grasp the complexities of protecting sensitive information online.
“Non-repudiation is like a virtual fingerprint that catches cyber criminals red-handed! Love it!”
I hate to burst your bubble, but non-repudiation is not some magical “virtual fingerprint” that catches cyber criminals. It’s just another piece of the puzzle in the world of cybersecurity. Let’s not overhype it, shall we?
“Non-repudiation is like having an unbreakable lock for your online transactions. Can’t argue with that!”