In the world of cyber security, there is a tactic that hackers use called baiting. Baiting is a technique used to lure unsuspecting individuals into compromising situations that can lead to security breaches. This article aims to shed light on the various baiting techniques employed by hackers and how you can protect yourself from falling victim to their deceptive tactics. So, if you’ve ever wondered what baiting is in the context of cyber security, you’ve come to the right place!
Definition of Baiting in Cyber Security
Explanation of what baiting means
Baiting, in the context of cybersecurity, refers to a technique used by attackers to trick individuals or organizations into performing unauthorized actions by enticing them with some form of bait. This bait can take various forms, such as an appealing offer, a fake website, or even a seemingly harmless email attachment. The aim of this deceptive tactic is to exploit human behavior and capitalization on human curiosity, greed, or trust in order to gain access to sensitive information or compromise computer systems.
Baiting is closely linked to social engineering tactics, as it takes advantage of human psychology and manipulation to achieve its objectives. Social engineering is the practice of manipulating people into divulging confidential information or performing certain actions that may compromise their cybersecurity. Baiting relies on similar principles by exploiting human vulnerabilities, including curiosity, greed, compassion, or even ignorance. By enticing individuals into taking actions they would not otherwise do, attackers can effectively exploit human vulnerabilities to gain access to sensitive information or compromise computer systems.
Examples of baiting incidents
Baiting incidents can take various forms, each with the common goal of deceiving and exploiting unsuspecting individuals. One common example is a USB baiting attack, where an attacker intentionally leaves infected USB drives in public places. The hope is that someone will pick up the USB drive, out of curiosity or need, and plug it into their computer. This action then triggers the malware contained within the USB drive, allowing the attacker to gain unauthorized access to the victim’s computer. Another example is baiting through phishing emails, where attackers send fraudulent emails that appear legitimate, usually with an urgent request or attractive offer, intending to entice recipients into clicking on malicious links or providing personal information.
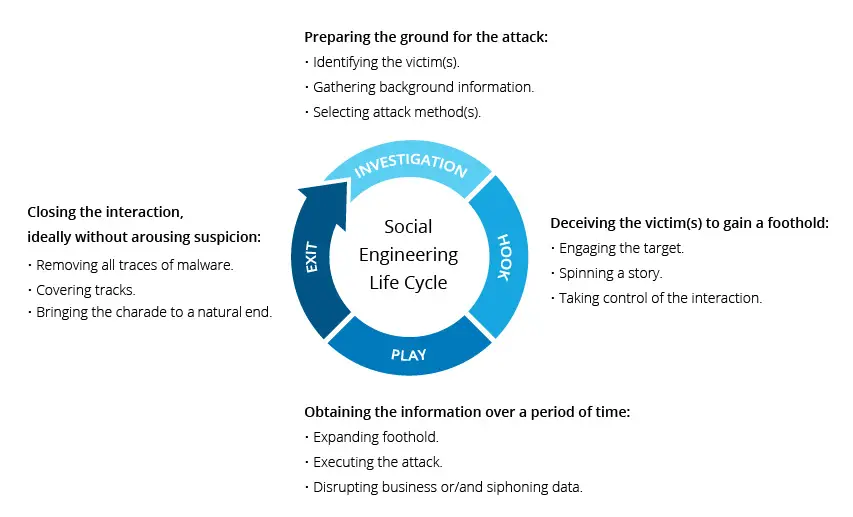
Understanding Social Engineering
Social engineering is a tactic used by cyber attackers to manipulate individuals into taking certain actions or divulging sensitive information. It often involves exploiting human psychology, such as trust, fear, or curiosity, to deceive and manipulate targets. social engineering attacks can occur in various forms, including phishing, pretexting, baiting, or even impersonating authority figures. The ultimate goal is to trick individuals into compromising their own security or providing access to sensitive information or systems.
Baiting is a specific technique employed within the broader umbrella of social engineering. It operates by using enticing baits to trick individuals into performing specific actions that may lead to compromises in cybersecurity. By exploiting human traits, such as curiosity or trust, baiting attacks effectively manipulate individuals into falling victim to sophisticated scams or attacks, often without them realizing they have been targeted.
Aside from baiting, there are several other types of social engineering attacks commonly employed by cyber criminals. Phishing is one such approach, where attackers send deceptive emails or messages masquerading as reputable sources, hoping to trick individuals into revealing sensitive information or clicking on malicious links. Pretexting involves creating a false scenario or pretext to manipulate individuals into divulging confidential information. Another common technique is impersonation, where attackers pose as someone else, such as a colleague, government official, or customer support representative, to deceive individuals into taking certain actions or providing information.
The Mechanics of Baiting Attacks
Steps involved in a baiting attack
Baiting attacks generally follow a series of steps, each designed to lure individuals into compromising their cybersecurity. The first step typically involves the creation of an enticing bait, such as an appealing offer, a fake website, or a seemingly harmless attachment. The attacker then strategically distributes the bait, either through physical means (like leaving infected USB drives in public spaces) or through digital channels (such as phishing emails or malicious websites). Once an individual takes the bait and performs the desired action, such as clicking a link or downloading a file, the attacker gains access to their system or information.
Analysis of baiting technique
The success of a baiting technique lies in its ability to exploit human vulnerabilities and capitalize on trust or curiosity. Attackers carefully craft their baits to appear enticing, often leveraging psychological techniques to elicit a response. The baits may present a sense of urgency, scarcity, or exclusivity to prompt individuals to act without carefully considering the consequences. Cybercriminals also use social engineering principles to establish credibility or legitimacy, manipulating individuals into believing the bait is genuine and trustworthy.
Role of the attacker and victim in a baiting scam
In a baiting scam, the attacker plays a strategic role by designing and executing the attack. They carefully choose their targets and craft the bait to maximize its appeal and effectiveness. The attacker’s objective is to deceive and manipulate victims into taking specific actions that lead to the attacker’s desired outcome, such as gaining access to sensitive information or compromising computer systems.
On the other hand, the victim, although targeted, may not be fully aware of the potential risks associated with the bait. They may innocently fall victim to the bait due to their curiosity, trust, or lack of cybersecurity awareness. It is crucial for individuals and organizations to educate themselves about common baiting techniques and develop a healthy skepticism towards unsolicited offers or requests, especially in the digital realm.
Common Baiting Techniques in Cyber Security
Phishing as a form of baiting
Phishing is one of the most common and effective forms of baiting techniques used by cyber attackers. It involves sending fraudulent emails or messages that appear genuine, often mimicking reputable organizations or individuals. These emails typically include enticing offers, urgent requests, or alarming messages to provoke an emotional response and prompt the recipient to take immediate action. Phishing baits often involve clicking on malicious links that lead to fake websites or downloading attachments infected with malware, allowing attackers to gain unauthorized access to systems or steal sensitive information.
Trojan horse baiting techniques
Trojan horse baiting is another prevalent technique used by attackers to exploit human curiosity or desire for free or pirated software. Attackers create software installers or application bundles that appear legitimate but contain hidden malicious components. These baited programs often promise desirable benefits, such as free software, games, or entertainment, tricking users into downloading and installing them. Once installed, the hidden malware can silently compromise the victim’s system or provide unauthorized access to the attacker.
Malware baiting via Email or Online credentials
Malware baiting through email or online credentials is a technique where attackers entice individuals to part with their personal information or inadvertently install malware. This bait often presents itself as a credible email, appearing to be from a reputable source, such as a bank or a trusted service provider. The email may ask for login credentials or personal information, luring recipients to click on malicious links or download infected attachments. In doing so, victims unknowingly expose themselves to various risks, including identity theft, financial loss, or compromise of their computer systems.

Identifying Baiting Attacks
Characteristics of common baiting attacks
There are several characteristics that can help identify common baiting attacks. One key characteristic is the use of enticing offers, whether it is a free download, a special promotion, or a once-in-a-lifetime opportunity. Baiting attacks also often employ urgency or fear tactics, pressuring individuals to take immediate action without considering potential risks. Another characteristic is the use of deception or impersonation, where attackers masquerade as trusted entities or individuals to gain the victim’s trust.
Detecting patterns in baiting scams
While baiting techniques constantly evolve, there are several patterns that can help individuals and organizations detect and protect against baiting scams. One pattern is the use of unsolicited communications, such as unexpected emails, messages, or social media interactions. These communications may contain offers or requests that seem too good to be true or create a sense of urgency. Another pattern is the presence of grammatical or spelling errors in communications, as attackers may not possess the same attention to detail as legitimate organizations. Being vigilant and scrutinizing digital communications for these patterns can help identify potential baiting attacks.
How to identify phishing and other forms of baiting
To identify phishing and other forms of baiting attacks, individuals and organizations must develop a keen sense of skepticism and adopt good cybersecurity practices. Some key indicators of phishing emails include grammatical or formatting errors, generic salutations, and requests for personal information or login credentials. Other signs of baiting techniques can include unexpected or unsolicited offers, urgent requests, or unusual website URLs. It is crucial for individuals to verify the legitimacy of communications independently, using official contact information instead of relying solely on the information provided in the communication itself.
Impact of Baiting Attacks
Damage caused by baiting
Baiting attacks can have significant consequences for both individuals and organizations. In terms of individuals, baiting attacks can result in identity theft, financial loss, or compromise of personal information. Attackers can gain unauthorized access to victims’ online accounts, steal sensitive data, or even use the information for further nefarious activities. In the case of organizations, baiting attacks can lead to data breaches, financial losses, reputational damage, or even legal ramifications. The release of sensitive customer data or the compromise of critical business systems can have far-reaching implications for the affected organization, including loss of customer trust and potential regulatory penalties.
Long term effects of a successful baiting attack
The long-term effects of a successful baiting attack can be devastating for both individuals and organizations. For individuals, the compromise of personal information can have long-lasting consequences, such as identity theft, financial ruin, or damage to one’s reputation. The emotional toll of being victimized in such a manner can also be significant. In the case of organizations, the aftermath of a successful baiting attack can include financial losses, legal battles, and diminished brand reputation. The loss of customer trust, coupled with potential regulatory penalties or lawsuits, can have long-term consequences on the profitability and sustainability of the organization.
Case studies of companies hit by baiting attacks
Numerous companies have fallen victim to baiting attacks, highlighting the severity and real-world impact of such incidents. One notable example is the 2013 Target data breach, where attackers used phishing emails to gain access to the retailer’s network. The attack resulted in the compromise of over 40 million credit and debit card records, along with personal information from approximately 70 million customers. Another case is the 2014 Sony Pictures Entertainment breach, where attackers used a baiting technique by sending fraudulent emails to employees, eventually leading to the theft and release of sensitive internal documents, emails, and intellectual property. These high-profile breaches serve as reminders of the importance of robust cybersecurity measures and vigilance against baiting attacks.

Preventative Measures Against Baiting
Security measures to prevent baiting
Implementing a range of security measures can significantly reduce the risk of falling victim to baiting attacks. These measures include regularly updating and patching software and operating systems to protect against known vulnerabilities. Employing strong and unique passwords for online accounts, as well as enabling multi-factor authentication whenever possible, adds an extra layer of protection. Installing reputable antivirus and anti-malware software can help detect and prevent the execution of malicious code. Additionally, individuals and organizations should exercise caution when clicking on unfamiliar links or opening email attachments, especially if they seem suspicious or have been unexpectedly received.
Role of cybersecurity software in preventing baiting
Cybersecurity software plays a vital role in preventing baiting attacks by providing ongoing protection against various types of malicious software and known attack vectors. Antivirus software can detect and block known threats, including malware, viruses, and Trojans, while anti-phishing software can identify and warn against fraudulent websites or phishing attempts. Firewalls and intrusion detection systems act as additional security layers, monitoring network traffic and blocking unauthorized access attempts. Keeping cybersecurity software up to date ensures it is equipped to detect and counter the latest baiting techniques and emerging threats.
Training and awareness as defensive strategies
Training and raising awareness among individuals and employees are critical defensive strategies against baiting attacks. Regular cybersecurity training sessions should cover topics such as identifying phishing emails, recognizing suspicious links or attachments, and adhering to secure browsing practices. Encouraging individuals to report potential baiting attacks or suspicious activities raises overall awareness within an organization and enables prompt action. By fostering a cybersecurity-conscious culture and maintaining vigilance, individuals can become the first line of defense against baiting attacks.
Responding to Baiting Attacks
Steps to take when a baiting attack is identified
When a baiting attack is identified, it is crucial to take immediate action to mitigate potential damage and limit the attacker’s access. The first step is to disconnect the affected device from the network to prevent further compromise. It is then recommended to notify the relevant authorities, such as the organization’s IT department or the cybersecurity team. Promptly reporting the incident allows for a timely investigation and the implementation of necessary remedial measures. Finally, affected individuals should change any compromised passwords and monitor their financial or personal accounts for any suspicious activities.
Reporting baiting incidents
Reporting baiting incidents to the appropriate authorities is crucial for several reasons. It facilitates the investigation and potentially helps to identify and apprehend the attackers, preventing further harm to others. Reporting incidents also contributes to broader awareness and threat intelligence, allowing authorities and cybersecurity professionals to analyze attack patterns, develop countermeasures, and share information to prevent future attacks. Depending on the jurisdiction and the nature of the attack, individuals or organizations can report baiting incidents to local law enforcement agencies, computer emergency response teams (CERTs), or relevant regulatory bodies.
How to retrieve lost data or compromised systems
Retrieving lost data or compromised systems after a baiting attack can be a challenging and time-sensitive process. It is crucial to involve cybersecurity professionals or incident response teams with expertise in handling such situations. These professionals can conduct detailed forensic investigations to identify the extent of the compromise and develop a plan for recovery. In some cases, data backups may be used to restore compromised information or systems. However, it is important to ensure that backups are secure and regularly tested to prevent backup data from being compromised or insufficient for recovery purposes. Timely response and expert assistance are vital to minimize the impact and facilitate the recovery process.

Cyber Security Laws and Baiting
Laws around baiting and cyber attacks
Numerous laws and regulations address cyberattacks, including baiting techniques, to deter and punish those engaged in such activities. The specifics of these laws can vary depending on the jurisdiction, but they generally criminalize unauthorized access to computer systems, theft of digital assets, or the distribution of malicious software. Additionally, laws may also cover offenses related to fraud, identity theft, or false representation, which can encompass certain baiting techniques. Examples of relevant acts and regulations include the Computer Fraud and Abuse Act (CFAA) in the United States, the Computer Misuse Act in the United Kingdom, and the European Union’s General Data Protection Regulation (GDPR).
Consequences for those caught baiting
The consequences for individuals caught baiting can be severe, ranging from substantial fines to lengthy imprisonment, depending on the jurisdiction and the severity of the offense. In addition to legal repercussions, individuals caught engaging in baiting attacks may face civil liabilities, such as being sued for damages resulting from their actions. Moreover, the social stigma associated with engaging in such criminal activities can have lasting personal and professional consequences. The severity of these consequences serves as a deterrent to potential baiting attackers and underscores the importance of robust cybersecurity practices.
Role of law enforcement in cyber security
Law enforcement agencies play a crucial role in cybersecurity and the fight against baiting attacks. They are responsible for investigating cybercrimes, including baiting incidents, and apprehending the culprits. By working closely with cybersecurity professionals, law enforcement agencies contribute to the identification and understanding of emerging threats, which helps in developing strategies to combat cyberattacks. Additionally, law enforcement agencies collaborate with international counterparts to investigate and prosecute cybercriminals across borders. Building strong partnerships between government agencies, private organizations, and law enforcement is essential for ensuring effective cybersecurity and countering baiting attacks.
Future trends in Baiting Techniques
Evolution of baiting techniques
Baiting techniques are expected to evolve and adapt to changing technological landscapes, as well as advancements in cybersecurity defenses. Attackers continually refine their tactics to bypass traditional security measures and exploit emerging vulnerabilities. One potential evolution of baiting techniques is the integration of artificial intelligence (AI) and machine learning (ML) capabilities, enabling attackers to create more sophisticated and convincing baits. Additionally, attackers may leverage emerging technologies, such as deepfakes, to deceive individuals by crafting realistic but fabricated content. As technology advances, so too will the techniques employed by attackers, necessitating continuous innovation in cybersecurity defenses.
New trends being observed in baiting
One emerging trend in baiting attacks is the convergence of physical and digital techniques. Attackers are increasingly combining physical baiting techniques, such as leaving infected USB drives in public spaces, with digital components, such as malware hidden within the USB drives. This hybrid approach targets both physical and digital vulnerabilities, increasing the likelihood of success. Another trend is the exploitation of current events, such as global pandemics or high-profile news events, to craft baits that capitalize on public interest and curiosity. Attackers tailor their baits to exploit individuals’ emotions and the desire for up-to-date information, increasing the effectiveness of their attacks.
How the future of technology might influence baiting techniques
The future of technology holds both promise and challenges in the realm of baiting techniques. As artificial intelligence and machine learning continue to advance, attackers may leverage these technologies to automate and personalize baiting attacks on a larger scale. Additionally, the proliferation of Internet of Things (IoT) devices presents new attack vectors, as attackers can leverage compromised devices to distribute baits or gain unauthorized access to networks. Furthermore, as technology becomes increasingly integrated into our daily lives, individuals and organizations must remain vigilant and adapt their cybersecurity practices to mitigate the risks associated with evolving baiting techniques.
In conclusion, baiting attacks remain a significant threat in the field of cybersecurity. By exploiting human psychology and vulnerabilities, attackers continue to develop sophisticated techniques to deceive and manipulate individuals into compromising their security. It is crucial for individuals and organizations to understand the various baiting techniques, learn to identify and prevent them, and remain vigilant against evolving threats. Implementing robust security measures, raising awareness through training, and collaborating with law enforcement are essential steps toward mitigating the risks associated with baiting attacks. As technology progresses, it is vital to stay abreast of emerging trends and adapt cybersecurity practices to effectively counter evolving baiting techniques.


