You’re about to gain a clear understanding of an essential technique in the world of cyber security – fuzzing. Fuzzing plays a crucial role in keeping our digital world safe from potential threats. This article will provide you with an overview of what fuzzing entails, highlighting its significance in identifying vulnerabilities and enhancing the resilience of computer systems. By the end, you’ll have a comprehensive understanding of how fuzzing contributes to the ever-evolving field of cyber security. Get ready to dive into this fascinating topic!

Definition of Fuzzing in Cyber Security
Basic conceptual understanding of fuzzing
Fuzzing, also known as fuzz testing or robustness testing, is a technique used in the field of cyber security to identify vulnerabilities in software applications. It involves generating and injecting invalid, unexpected or random data inputs into a target system to trigger unexpected behaviors, crashes, or security flaws. By doing so, fuzzing helps cybersecurity professionals uncover flaws and weaknesses in software that could potentially be exploited by malicious attackers.
Importance of fuzzing in cyber security
Fuzzing plays a critical role in the field of cyber security as it helps to identify vulnerabilities that may otherwise go unnoticed. In a world where cyber threats are constantly evolving, it is essential to have robust security measures to protect sensitive information. Fuzzing allows organizations to proactively identify and address security flaws in their software applications, improving the overall security posture. By identifying and fixing vulnerabilities before they can be exploited, organizations can enhance their resilience against cyber attacks and minimize potential damages.
Origins of Fuzzing
Historical overview of fuzzing
Fuzzing has its roots in the early days of computer science and software development. The technique was first introduced by Professor Barton Miller from the University of Wisconsin in the late 1980s. The initial motive behind fuzzing was to uncover software bugs and crash-inducing inputs. Over time, fuzzing techniques have evolved to focus on finding security vulnerabilities and reducing the potential for exploitation.
Initial applications in computer security
The initial applications of fuzzing in computer security were limited to uncovering crash-inducing bugs. However, as the field of cyber security evolved, fuzzing became an important tool in identifying security vulnerabilities. By injecting unexpected or malicious inputs, fuzzing can reveal weaknesses such as buffer overflows, input validation failures, and memory corruption issues. As a result, the adoption of fuzzing as a proactive security measure has grown significantly in recent years.
Types of Fuzzing Techniques
Generation-based fuzzing
Generation-based fuzzing involves creating test cases by generating valid and invalid inputs based on various criteria such as file formats, network protocols, or application-specific data structures. This technique aims to exercise different branches of the software’s execution path and detect vulnerabilities that may be triggered by unexpected or malformed inputs.
Mutation-based fuzzing
Mutation-based fuzzing, also known as random fuzzing, involves modifying existing inputs by mutating them randomly. This fuzzing technique is based on the assumption that even a small change to an input can lead to the discovery of new vulnerabilities. By randomly altering input values, mutation-based fuzzing aims to explore different program behaviors and test the resilience of the software under unexpected conditions.
Evolutionary fuzzing techniques
Evolutionary fuzzing techniques leverage genetic algorithms and feedback-driven approaches to generate and refine test cases. These techniques start with a set of initial test cases and iteratively improve them based on their ability to trigger vulnerabilities. By applying evolutionary principles, such as mutation and reproduction, these techniques can automatically generate optimized test cases that are more likely to uncover vulnerabilities.
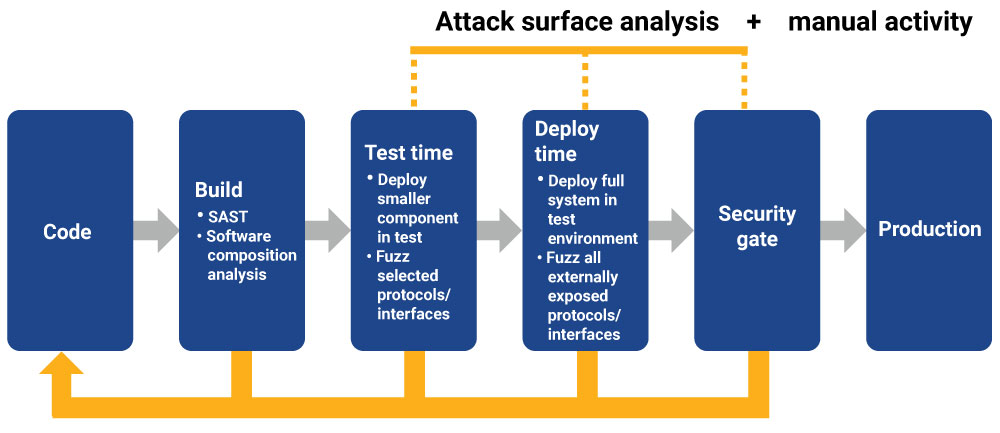
Process of Fuzzing in Cyber Security
Identification of target system
The first step in the fuzzing process is to identify the target system that will be subjected to fuzz testing. This could be a specific software application, a network protocol, or even a hardware device. It is crucial to understand the target system’s specifications, input requirements, and potential areas of vulnerability to effectively design and execute fuzzing tests.
Generation or mutation of test cases
Once the target system is identified, the next step is to generate or mutate test cases. These test cases are designed to exercise the various functionalities and inputs of the target system. Generation-based fuzzing techniques generate test cases based on predefined specifications, while mutation-based techniques modify existing test cases randomly. The choice of fuzzing technique depends on the specific requirements and objectives of the fuzzing campaign.
Execution and monitoring of test cases
After the test cases are generated or mutated, they are executed against the target system. During execution, the behavior of the target system is monitored and observed for any unexpected or abnormal responses. This includes monitoring for crashes, memory leaks, error messages, or any other indications of potential vulnerabilities. Tools and frameworks designed specifically for fuzzing assist in the automated execution and monitoring of test cases, making the process more efficient and scalable.
Analysis of results and identification of potential vulnerabilities
Once the fuzzing campaign is completed, the results are analyzed to identify potential vulnerabilities and security issues. This involves examining crash reports, logs, stack traces, and other relevant data to pinpoint the root causes of observed failures. The analysis phase requires expertise in reverse engineering and vulnerability discovery to understand the implications of the identified vulnerabilities and assess their potential impact on the security of the system.

Tools Used in Fuzzing
Overview of common fuzzing tools
There are various fuzzing tools available in the market that facilitate the fuzzing process. Some popular open-source fuzzing frameworks include AFL (American Fuzzy Lop), libFuzzer, and Peach Fuzzer. These tools provide the necessary infrastructure and mechanisms for generating and executing fuzz test cases, as well as analyzing the results. Commercial fuzzing tools such as Codenomicon Defensics and Synopsys Defensics offer additional features and support, but often come with a cost.
Open source versus proprietary tools
The choice between open-source and proprietary fuzzing tools depends on factors such as budget, desired level of automation, and availability of support. Open-source tools are typically more accessible and affordable, while proprietary tools often provide more advanced capabilities and dedicated support teams. It is important to evaluate the specific needs and resources of an organization before deciding on the most suitable fuzzing tool.
Choosing the right tool for the job
When selecting a fuzzing tool, it is essential to consider the target system’s requirements, the complexity of the software, and the available resources. The chosen tool should be compatible with the target system’s programming language, provide coverage for relevant protocols and file formats, and offer efficient test case generation and monitoring mechanisms. Conducting proper research and seeking recommendations from experts can help in selecting the most effective and appropriate tool for the job.
Benefits of Fuzzing in Cyber Security
Proactive identification of vulnerabilities
Fuzzing enables organizations to proactively identify vulnerabilities in their software applications. By subjecting the target system to unexpected and potentially malicious inputs, fuzzing can quickly uncover weaknesses that may be exploited by attackers. Through this proactive approach, organizations can mitigate security risks before they are exploited and minimize potential damages caused by cyber attacks.
Improving system robustness
By uncovering vulnerabilities and weaknesses, fuzzing helps organizations identify areas where their software applications may be lacking in terms of robustness. This allows developers to enhance the resilience and reliability of their systems, making them more resistant to unexpected inputs and potential security breaches. By continuously fuzzing and improving their software, organizations can build a stronger defense against cyber threats.
Reducing potential for exploitation by malicious entities
By proactively identifying and fixing vulnerabilities, fuzzing reduces the potential for exploitation by malicious entities. Uncovered vulnerabilities can be addressed before they are discovered and leveraged by attackers. This helps organizations maintain the integrity of their systems and protect sensitive information from unauthorized access, manipulation, or theft. Fuzzing acts as an additional layer of defense, ensuring that potential vulnerabilities are addressed before they can be exploited.

Limitations and Challenges of Fuzzing
Time and resource consumption
Fuzzing can be a time and resource-consuming process, especially when conducting comprehensive and exhaustive testing. Generating and executing large volumes of test cases requires significant computational power and storage capacity. Additionally, analyzing the results and identifying true vulnerabilities from a flood of false positives can be a challenging and time-consuming task. Organizations need to carefully consider the trade-offs between the time and resources invested in fuzzing and the potential benefits gained.
Missed vulnerabilities due to random nature of testing
Fuzzing relies on random or semi-random inputs to uncover vulnerabilities, which means that there is a possibility of missing certain vulnerabilities that require specific inputs or conditions to trigger. Fuzzing may not be able to uncover vulnerabilities that are deeply buried within the software or require certain sequences of actions to manifest. Therefore, it is important to complement fuzzing with other testing techniques and security measures to ensure comprehensive coverage.
Complexity of identifying and fixing uncovered vulnerabilities
Identifying and fixing uncovered vulnerabilities can be a complex task, especially when dealing with intricate software systems. The root causes of vulnerabilities may not always be apparent, requiring in-depth analysis and reverse engineering to understand the underlying issues. Patching vulnerabilities could also involve significant code changes, regression testing, and coordination with various stakeholders, which adds to the complexity of the overall process. Organizations need to allocate resources and expertise to effectively address uncovered vulnerabilities.
Case Studies on the Use of Fuzzing
Fuzzing in large-scale tech companies
Many large-scale tech companies, such as Google, Microsoft, and Apple, have successfully employed fuzzing techniques to enhance the security and reliability of their software products. Google, for example, has been actively using fuzzing for years and has even developed its own fuzzing infrastructure called OSS-Fuzz. By subjecting their software to extensive fuzz testing, these companies can proactively discover and patch vulnerabilities, minimizing the potential impact of security breaches.
Fuzzing in government security audits
Government organizations and security agencies also utilize fuzzing techniques during security audits and evaluations. Fuzzing helps identify potential vulnerabilities in critical systems, ensuring that they meet the required security standards and can withstand potential attacks. By leveraging fuzzing as part of the audit process, governments can strengthen their cyber defense capabilities and protect national assets and sensitive information from adversaries.
Use of fuzzing in ethical hacking
Ethical hackers, also known as security researchers or white hat hackers, utilize fuzzing techniques to identify vulnerabilities and report them to software vendors or security authorities. By fuzzing software applications and systems, ethical hackers can assist in uncovering critical security flaws before malicious actors can exploit them. Fuzzing plays a crucial role in the responsible disclosure of vulnerabilities and facilitates the development of more secure software in collaboration with the security community.
Future Trends in Fuzzing
Integration of AI and machine learning in fuzzing processes
The integration of artificial intelligence (AI) and machine learning (ML) techniques in fuzzing processes is an emerging trend in the field. By leveraging AI and ML algorithms, fuzzing can become more intelligent and adaptive in generating test cases and identifying potential vulnerabilities. These techniques can be used to optimize the fuzzing process, prioritize test cases, and even automatically generate patches for discovered vulnerabilities. The combination of AI and fuzzing has the potential to revolutionize the way vulnerabilities are identified and addressed in the future.
Potential future developments in fuzzing techniques
Fuzzing techniques are continuously evolving to keep up with the changing landscape of software and cyber threats. Advanced mutation and generation algorithms, along with improved analysis and feedback mechanisms, are expected to enhance the effectiveness and efficiency of fuzzing. Additionally, new techniques such as symbolic execution, concolic testing, and coverage-guided fuzzing are gaining attention and being integrated into existing fuzzing frameworks. Future developments in fuzzing techniques are likely to focus on increasing automation, reducing false positives, and providing higher code coverage.
The role of fuzzing in the age of IoT and 5G
As technology advances and the Internet of Things (IoT) and 5G networks become more prevalent, the role of fuzzing in the field of cyber security becomes even more critical. The increased connectivity and complexity introduced by IoT devices and 5G networks create new attack vectors and security challenges. Fuzzing can help identify vulnerabilities in IoT devices, network protocols, and communication channels, ensuring the security and privacy of connected devices and the data they handle. Fuzzing will continue to play a crucial role in securing the digital infrastructure in the age of IoT and 5G.
Best Practices in Fuzzing
Administering fuzzing tests on a regular basis
To ensure a robust security posture, it is important to administer fuzzing tests on a regular basis. This allows organizations to continuously identify and address vulnerabilities in their software applications. Implementing a systematic and scheduled approach to fuzzing ensures that potential weaknesses are regularly discovered and mitigated, reducing the chance of successful attacks.
Optimizing fuzzing processes through automation
Automation is key to optimizing fuzzing processes and making them more efficient. By utilizing automated test case generation, execution, and result analysis, organizations can save time and resources, increase coverage, and improve the scalability of their fuzzing campaigns. The use of dedicated fuzzing frameworks and tools significantly simplifies the automation process and enables organizations to conduct fuzzing at scale.
Continually updating and refining fuzzing methods to cope with evolving system complexities
Software systems are constantly evolving, and new vulnerabilities emerge as a result of updated features, patches, or new attack techniques. It is essential to continually update and refine fuzzing methods to keep up with these changes. Staying informed about the latest fuzzing techniques and maintaining a proactive approach to fuzzing ensures that the security of software applications remains resilient against emerging threats.
Importance of leveraging fuzzing as part of a holistic cyber security approach
Fuzzing should be viewed as one component of a holistic cyber security approach. Combining fuzzing with other security practices, such as static code analysis, penetration testing, and secure coding practices, strengthens the overall security posture of an organization. By integrating fuzzing into the entire software development lifecycle and following secure coding practices, organizations can reduce the likelihood of vulnerabilities and enhance the security of their systems.
In conclusion, fuzzing is a powerful technique in the field of cyber security that helps identify vulnerabilities and ensure the robustness of software applications. By injecting unexpected and potentially malicious inputs, fuzzing enables organizations to proactively address security flaws before they can be exploited by attackers. Despite its limitations and challenges, fuzzing continues to evolve, incorporating AI and ML techniques, and playing a crucial role in securing modern technologies such as IoT and 5G networks. By implementing best practices and fostering a holistic cyber security approach, organizations can leverage fuzzing to enhance their security posture and protect their valuable assets from cyber threats.