In “Understanding Smishing Attacks: A Cyber Security Perspective,” you will gain valuable insights into the world of cyber security and discover what smishing refers to. This article sheds light on the intricacies of smishing attacks – a form of cyber security threat that targets individuals through text messages and phone calls. By providing you with a comprehensive understanding of this alarming phenomenon, you will be better equipped to safeguard yourself against potential smishing attacks and protect your personal information from falling into the wrong hands. Stay informed and stay secure!
Understanding Smishing
Definition of Smishing
Smishing is a term that combines the words “SMS” and “phishing,” referring to a type of cyber attack that utilizes text messages (SMS) to deceive and manipulate individuals into revealing sensitive information or performing malicious actions. In a smishing attack, perpetrators pose as legitimate organizations or individuals, sending seemingly innocent SMS messages to potential victims. These messages often aim to exploit human vulnerabilities such as curiosity, urgency, or fear in order to convince recipients to disclose personal information, click on malicious links, or download harmful software.
Role of Smishing in Cyber Attacks
Smishing has become an increasingly prominent method employed by cybercriminals due to its effectiveness in reaching a wide range of potential targets. In the ever-evolving landscape of cyber attacks, smishing offers perpetrators a direct line of communication with their victims, bypassing some of the typical security measures that have been implemented to counter phishing attacks. Smishing attacks serve as a key component in multi-layered cyber attacks, where criminals combine various techniques to exploit vulnerabilities in individuals and organizations alike.
General statistics about Smishing
Statistics surrounding smishing attacks highlight their prevalence and the significant impact they have on individuals and businesses. According to recent reports, smishing attacks have been on the rise, accounting for a substantial portion of all cyberattacks. In fact, it is estimated that smishing constitutes approximately 30% of all phishing attacks. With the widespread use of mobile devices and the growing reliance on SMS messages for communication, smishing has proven to be a formidable threat that continues to evolve and adapt to the shifting cybersecurity landscape.
Historical Perspective of Smishing Attacks
Origination of Smishing
Smishing attacks can be traced back to the early 2000s when mobile phone usage began to surge. As more individuals started communicating through text messages, cybercriminals recognized the potential to exploit this new avenue. They adapted the tactics employed in conventional phishing, which targeted email users, to send deceptive messages via SMS. This marked the birth of smishing attacks, with the earliest recorded instances focusing on impersonating financial institutions and enticing recipients to disclose their account details or other sensitive information.
Growth and Evolution of Smishing
Over the years, smishing attacks have grown in sophistication and complexity. With advancements in technology, cybercriminals have been able to augment their deceptive tactics, making it increasingly difficult for individuals to differentiate between genuine and malicious SMS messages. Smishing attacks have evolved to encompass a broader range of subject matter, including fake delivery notifications, prize giveaways, security alerts, and even personal messages intended to exploit emotional vulnerabilities.
Impact of Smishing over the Years
The impact of smishing attacks has been significant, both in terms of financial losses and psychological distress. The continuous growth and adaptation of smishing techniques have led to an alarming increase in successful attacks, causing considerable financial harm to individuals and organizations. Additionally, the psychological effects on victims cannot be overstated, as smishing attacks often compromise their sense of security, leaving them vulnerable and distrustful of digital communication channels.
How Smishing Attacks Work
Techniques used in Smishing
Smishing attacks employ a range of techniques to deceive and manipulate their targets. These include:
- Caller ID Spoofing: Perpetrators use technology to modify the sender information displayed on recipients’ devices, making the SMS message appear to be from a legitimate source.
- Urgency and Fear: Smishing messages create a sense of urgency or fear in recipients, pressuring them to take immediate action without thoroughly evaluating the legitimacy of the request.
- Clickbait: Attackers often include enticing offers or clickbait in their smishing messages to entice recipients into clicking on malicious links.
- Social Engineering: Smishing leverages social engineering tactics to exploit human vulnerabilities, such as curiosity, trust, or the desire for rewards, to persuade recipients to disclose sensitive information willingly.
Example of a Smishing Attack
To better understand how smishing attacks unfold, consider the following hypothetical scenario:
You receive a text message from what appears to be your bank, informing you that your account has been compromised and requires immediate action. The message instructs you to click on a link to review the suspicious transactions and prevent any further unauthorized access. The urgency and fear instilled by this message may cause you to act without considering the possibility of it being a smishing attack. If you click on the provided link, you may be directed to a fraudulent website that mimics your bank’s login page, tricking you into entering your credentials and handing them over to the cybercriminals.
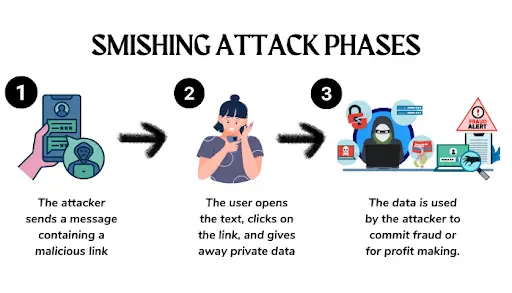
Phases of a Smishing Attack
Smishing attacks generally follow a sequence of phases that culminate in the successful compromise of the targeted individual or organization. These phases typically include:
- Research and Planning: Cybercriminals identify potential targets and gather information necessary to personalize the smishing messages.
- Message Crafting: Attackers create persuasive and often urgent SMS messages designed to evoke specific behavioral responses in the recipients.
- Distribution: The smishing messages are sent out to a large number of potential victims, often exploiting purchased phone number lists or data breaches.
- Victim Manipulation: Upon receiving the smishing messages, the cybercriminals use psychological tactics to manipulate recipients into taking the desired actions, such as clicking on a link or sharing sensitive information.
- Exploitation: Victims who fall for the smishing attack provide the attackers with the opportunity to obtain personal data, install malware, or initiate other malicious activities.
Difference Between Smishing and Phishing
Understanding Phishing
While smishing and phishing share similar objectives, they differ in the channels through which they are executed. Phishing primarily relies on deceptive email messages, whereas smishing focuses on exploiting vulnerabilities through text messages. Phishing attacks cast a broader net due to the prevalence of email usage, whereas smishing targets individuals who primarily rely on SMS communication on their mobile devices.
Comparative Analysis of Smishing and Phishing
Both smishing and phishing attacks rely on social engineering techniques to deceive their victims. However, smishing offers a more direct line of communication, often creating a stronger sense of urgency or fear due to the immediacy of the text messages. Additionally, smishing attacks can be tailored to specific individuals or groups, making them appear more personalized and convincing.
Unique Attributes of Each Method
While smishing and phishing attacks have many similarities, they also possess unique attributes that set them apart. Smishing attacks have the advantage of bypassing some email security measures and directly reaching users on their mobile devices, where people typically have a higher level of trust. On the other hand, phishing attacks can exploit the wider information and functionality available through email, such as embedded links, attachments, and sophisticated social engineering techniques.

Common Smishing Scams
Types of Smishing Scams
Smishing scams can take on various forms, targeting different aspects of individuals’ lives and exploiting their vulnerabilities. Some common types of smishing scams include:
- Financial Scams: Impersonating banks, credit card companies, or online payment platforms to trick individuals into disclosing their financial information.
- Prize Scams: Notifying recipients that they have won a prize or a contest, encouraging them to share personal information or pay a fee to claim the reward.
- Delivery Scams: Pretending to be a delivery service and requesting individuals to click on a link to track or reschedule a package delivery, potentially leading to malware installation.
- Government Impersonation: Sending messages claiming to be from government departments or authorities, demanding payments or personal information under false pretenses.
Existing Threats and Scams
Smishing attacks are continually evolving, with cybercriminals devising new scams to exploit unsuspecting individuals. Some existing threats and scams include:
- COVID-19 Related Scams: Exploiting the ongoing pandemic, smishing attacks have increased, with messages claiming to provide updates, safety guidelines, or vaccine registration links.
- Charity Scams: Preying on people’s willingness to donate, smishing attacks impersonate charitable organizations, seeking donations for a cause that does not exist.
- Online Shopping Scams: Sending texts about enticing offers or limited-time discounts to lure individuals into sharing personal information or making purchases from fraudulent websites.
Examples of Real-world Smishing Scams
Real-world examples of smishing scams serve as cautionary tales, demonstrating the lengths to which cybercriminals will go to deceive their victims.
- Apple ID Verification Scam: A widespread smishing scam involved sending SMS messages claiming that the recipient’s Apple ID had been compromised and directing them to a fraudulent website to verify their account details.
- PayPal Account Verification Scam: Cybercriminals sent smishing messages, purporting to be from PayPal, requesting individuals to validate their accounts by clicking on a link and submitting their login credentials and personal information.
- Bank Phishing Scam: Smishing attacks targeting banks have become increasingly common, with perpetrators sending SMS messages pretending to be from the bank’s fraud department, urging victims to click on a link to resolve an urgent issue.
The Impact of Smishing Attacks
Financial losses caused by Smishing
Smishing attacks can result in significant financial losses for individuals and organizations alike. Victims who inadvertently disclose their banking credentials, credit card details, or other sensitive financial information may find themselves falling victim to fraudulent transactions or identity theft. According to industry reports, smishing attacks have resulted in millions of dollars in losses, impacting both personal finances and corporate bottom lines.
Psychological effects on victims
In addition to the financial consequences, smishing attacks have profound psychological effects on victims. The breach of trust, violation of privacy, and loss of security that individuals experience can lead to heightened anxiety, stress, and a general sense of unease. Victims may also become more skeptical and hesitant to trust future digital communication, impacting their overall well-being and mental health.
Reputational Damage for Businesses
Smishing attacks can lead to reputational damage for businesses whose names or branding have been exploited by cybercriminals. When customers or clients associate a company with a smishing attack, trust is eroded, and confidence in the organization’s ability to protect sensitive information diminishes. Rebuilding trust and credibility takes time and concerted effort, and the negative impact on a business’s image can have long-lasting consequences.
Preventing and Detecting Smishing Attacks
Security Measures to Prevent Smishing
To mitigate the risk of falling victim to smishing attacks, individuals and organizations can implement various security measures, including:
- Education and Awareness: Educating oneself about the techniques employed in smishing attacks can empower individuals to recognize and respond appropriately to suspicious messages.
- Message Filters: Utilizing spam filters or mobile security applications that identify and block potential smishing messages can significantly reduce the risk of exposure to such attacks.
- Two-Factor Authentication: Enabling two-factor authentication for all relevant accounts adds an extra layer of protection, making it more challenging for attackers to gain unauthorized access.
- Verification of Requests: Always verify requests, especially those involving sensitive information or financial transactions, through trusted channels such as directly contacting the sender by phone or visiting their official website.
Detecting Suspicious SMS, Reporting Smishing Incidents
Detecting suspicious SMS messages is crucial for preventing smishing attacks. Some indicators of a potential smishing message include:
- Unusual Sender Information: Pay attention to the sender’s phone number or alphanumeric sender ID, especially if it is unfamiliar or contains spelling mistakes.
- Urgency or Fear Tactics: Be cautious of messages that create a sense of urgency, demand immediate action, or threaten dire consequences for non-compliance.
- Suspicious Links or Attachments: Exercise caution when a message contains unexpected links, shortened URLs, or attachments, as these could lead to malicious websites or malware downloads.
If you suspect a smishing attack or have fallen victim to one, it is crucial to report it promptly. Contact your mobile service provider, local law enforcement, and any relevant organizations, such as your bank or credit card company, to inform them of the incident. Reporting smishing incidents helps create awareness and aids in the identification and apprehension of cybercriminals.
Technological Solutions to Smishing
Tools and Technologies for Protection
Technological solutions play a significant role in combating smishing attacks. Some tools and technologies that can aid in protection include:
- Mobile Security Applications: Installing reputable mobile security applications can help detect and block potential smishing messages before they reach the recipient’s device.
- SMS Gateways: Organizations can implement SMS gateways to filter incoming messages, identify potential smishing messages, and provide an additional layer of security for their employees.
- Threat Intelligence Platforms: Utilizing threat intelligence platforms allows organizations to stay informed about emerging smishing techniques, patterns, and known malicious sender information, enabling proactive protection measures.
Role of Machine Learning and AI in Combating Smishing
Machine learning and artificial intelligence (AI) play a vital role in detecting and mitigating smishing attacks. By analyzing patterns and characteristics of smishing messages, machine learning algorithms can identify and flag potentially malicious messages with a high degree of accuracy. AI-powered systems can adapt and update their detection mechanisms based on real-time data, staying ahead of evolving smishing techniques.
Assessing the Effectiveness of Technological Solutions
As smishing attacks continue to evolve, it is essential to continually assess the effectiveness of technological solutions. Regular updates and improvements to mobile security applications, SMS gateways, and threat intelligence platforms are necessary to ensure they can effectively detect, block, and report smishing attacks. Collaborative efforts between security researchers, industry stakeholders, and regulatory bodies are key to staying proactive and adaptive in the face of ever-changing cyber threats.
Legal Perspectives and Policies on Smishing
Existing Cyber Security Laws against Smishing
Numerous countries have enacted legislation and regulations specifically targeting cybercrime, including smishing attacks. Laws differ between jurisdictions, with penalties imposed for offenses related to smishing, such as unauthorized access, identity theft, fraud, and violation of consumer privacy. These laws aim to hold perpetrators accountable for their actions and provide legal recourse for victims.
Challenges in Policy Implementation
While cyber security laws exist to address smishing attacks, their effective implementation poses significant challenges. Smishing attacks are often conducted across borders, making it difficult to track down perpetrators and ensure jurisdictional cooperation. Furthermore, the dynamic nature of cyber threats necessitates the continuous adaptation of laws and policies to keep pace with emerging smishing techniques.
Future Policy Recommendations
To strengthen the prevention, detection, and prosecution of smishing attacks, several policy recommendations can be considered:
- International Collaboration: Governments, law enforcement agencies, and industry organizations should enhance collaboration at an international level, establishing frameworks to facilitate information sharing, cross-border investigations, and the harmonization of legal measures against smishing.
- Public-Private Partnerships: Encouraging public-private partnerships can foster knowledge sharing, technological innovation, and coordinated efforts in combating smishing attacks.
- Education and Awareness Campaigns: Governments should invest in educational programs to raise awareness about smishing attacks and provide individuals with the tools and knowledge to identify and report suspicious messages effectively.
- Regular Legal Updates: Ongoing evaluation of existing laws and regulations is crucial to ensure they remain relevant and effective in combating emerging smishing techniques. Regular legal updates can address jurisdictional challenges and provide guidelines for law enforcement agencies.
The Future of Smishing
Predicted Trends in Smishing
As technology advances, it is anticipated that smishing attacks will continue to evolve and adapt to emerging communication platforms and channels. Some predicted trends in smishing include:
- Voice Phishing: With the increasing use of voice assistants and voice communication, smishing attacks may transition to exploit voice messaging systems, targeting individuals through phone calls or voice-based communication platforms.
- Enhanced Personalization: Smishing attacks are likely to become even more targeted and personalized, leveraging extensive data sets on individuals to create more convincing and tailored messages.
- Growing IoT Vulnerability: As the Internet of Things (IoT) expands, smishing attacks could exploit vulnerabilities in connected devices, such as smart home systems or wearables, to manipulate individuals and access their personal information.
Emerging Smishing Techniques
The relentless efforts of cybercriminals to evade detection and deceive their targets drive the emergence of new smishing techniques. Some emerging smishing techniques include:
- Deepfake SMS: Advances in deepfake technology may lead to the creation of convincing and realistic smishing messages, further blurring the line between legitimate and fraudulent communication.
- Social Media Exploitation: With the increasing reliance on social media platforms, cybercriminals may exploit these channels to gather information, engage with potential victims, and launch smishing attacks using messaging features on these platforms.
Role of Continuous Awareness and Education
Continuous awareness and education play a vital role in mitigating the risks associated with smishing attacks. Individuals should stay informed about emerging smishing techniques, recognize the signs of a potential attack, and adopt best practices for securing their personal information. Ongoing educational campaigns, collaboration between industry stakeholders, and the integration of cybersecurity education into formal curriculum can contribute to enhancing the public’s resilience against smishing attacks.


“Wow, I never knew smishing attacks were so prevalent! Definitely need to stay alert!”
Wow, smishing attacks are getting more sneaky and dangerous! Better watch out for those phishing texts! 📱💀
Wow, I never realized how sneaky smishing attacks could be! Scary stuff! 😱📲
“Wow, smishing attacks are getting smarter! Can’t believe scammers are using emojis now 😱”
“Wow, smishing attacks sound terrifying! Who knew cyber criminals could be so sneaky?”
Actually, it’s common knowledge that cyber criminals are always finding new ways to exploit unsuspecting victims. Smishing attacks are just the tip of the iceberg. Stay informed and protect yourself, or remain oblivious and become their next target. Your choice.
“Wow, smishing attacks are no joke! Who knew text messages could be so dangerous? 😱”