In the world of cybersecurity, it is crucial to grasp the significance of Acceptable Use Policy (AUP). This integral set of rules and guidelines dictates how individuals and organizations should utilize technology and digital resources. Whether it’s in an educational setting, a corporate environment, or even at home, understanding AUP ensures a safer ecosystem for everyone. This article will explore the ins and outs of AUP, shedding light on its importance and how it contributes to maintaining cybersecurity. So, let’s dive in and unravel the mysteries of AUP together!
Defining AUP in Cyber Security
Exploring the Acronym AUP
AUP stands for Acceptable Use Policy, which is a set of guidelines and rules established by organizations to define the acceptable and appropriate use of their IT resources. It serves as a framework for users’ behavior and ensures that they adhere to specific standards and practices related to the use of technology and network resources.
Relevance of AUP in Cyber Security
In the ever-evolving landscape of cyber threats, the relevance of AUP in cyber security cannot be overstated. AUP plays a crucial role in safeguarding organizations from various security risks, including unauthorized access, data breaches, and misuse of resources. It sets the expectations for employees and users, promoting responsible and secure digital practices.
Understanding the Purpose of AUP
The Role of AUP in Cyber Security
The primary role of AUP in cyber security is to establish guidelines and regulations that govern users’ actions regarding the use of technology resources. By defining acceptable behavior and outlining security practices, AUP helps organizations mitigate the risk of cyber attacks and protect their sensitive information.
Importance of Having a Clear AUP
Having a clear and well-communicated AUP is paramount in ensuring a secure cyber environment. It sets the expectations for employees, contractors, and users, helping them understand the boundaries of acceptable use and the potential consequences of non-compliance. A well-defined AUP promotes security awareness and helps prevent inadvertent security breaches.
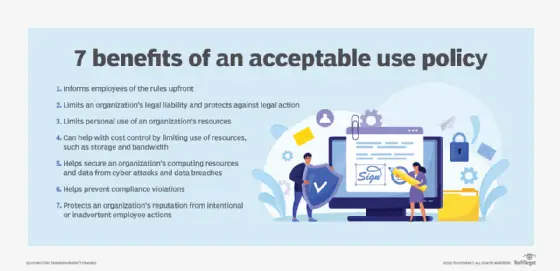
Components of a Robust AUP
Key Elements of an AUP
A robust AUP typically consists of several key elements. Firstly, it defines the scope and purpose of the policy, making it clear what resources it covers and the objectives it aims to achieve. Secondly, it establishes the acceptable use guidelines for technology resources, outlining prohibited activities such as unauthorized access, data breaches, or sharing confidential information. Additionally, it should address the consequences of non-compliance and provide a clear process for reporting violations.
Features of a Good AUP
A good AUP should exhibit certain features to enhance its effectiveness. It should be concise, clearly written, and easily understandable, ensuring that all users can comprehend and adhere to its guidelines. It should also be regularly updated to reflect changes in technology and emerging cyber threats. Moreover, a good AUP should be supported by organizational leadership, emphasizing the importance of following the policy to ensure a secure digital environment.
How AUP Enhances Cyber Security
Controlling User Behavior With AUP
AUP plays a crucial role in controlling user behavior and promoting responsible digital practices. By clearly defining acceptable use guidelines, it sets expectations for employees and users, ensuring they understand the boundaries and limitations of technology resources. This helps prevent risky behaviors that could lead to security breaches, such as downloading malicious software or visiting unauthorized websites.
Reducing Cyber Security Risks through AUP
An effective AUP can significantly reduce cyber security risks within an organization. By addressing potential vulnerabilities, such as sharing passwords or accessing sensitive data without authorization, AUP acts as a preventive measure against security incidents. It helps create a culture of security awareness and encourages responsible use of technology, ultimately minimizing the likelihood of cyber attacks and data breaches.

Implementing AUP in an Organization
Steps in Setting Up an AUP
Implementing AUP in an organization requires a systematic approach. Firstly, it is important to involve key stakeholders, such as IT, HR, and legal departments, in drafting the policy. This ensures that all relevant perspectives are considered. Once the AUP is developed, it should be communicated clearly to all employees and users, preferably through training sessions or orientation programs. Regular monitoring and enforcement of the policy should also be established to ensure compliance.
Challenges in AUP Implementation
Implementing AUP can present certain challenges. Resistance from employees or users who are accustomed to certain behaviors or practices that may violate the policy is one such challenge. Addressing this resistance involves educating individuals about the potential risks and benefits of adhering to the AUP. Ensuring consistent enforcement of the policy can also be challenging, as it requires ongoing monitoring and disciplinary actions when violations occur. Overcoming these challenges is vital to the successful implementation of the AUP.
Familiarizing with AUP Terms and Conditions
Typical Provisions in an AUP
AUPs typically include several provisions that define the terms and conditions of usage. These provisions often cover areas such as the acceptable use of email systems, internet browsing, social media usage, and the handling of confidential information. They may also include guidelines on software installation, password management, and reporting security incidents. These provisions help users understand their rights, responsibilities, and the boundaries within which they must operate.
Understanding Legal Consequences under AUP
Violating an AUP can have legal consequences for individuals or organizations. Depending on the severity of the violation and the jurisdiction, legal repercussions may include disciplinary action, termination of employment, civil liabilities, or even criminal charges. Understanding the potential legal consequences under an AUP helps create a culture of compliance and accountability, encouraging users to adhere to the policy.
AUP and Legal Aspects in Cybercrime
AUP in the Context of Cyber Laws
AUPs often align with cyber laws and regulations to ensure legal compliance. Many countries have specific regulations related to data protection, privacy, and cybercrime. AUPs should address these legal requirements and ensure that users are aware of their obligations to comply with relevant legislation. By incorporating legal aspects into AUPs, organizations can strengthen their cyber security posture and avoid violations that may lead to legal consequences.
Legal Effects of Violating AUP
Violating an AUP can have serious legal effects. Depending on the jurisdiction and the breach’s nature, individuals or organizations may face civil lawsuits or criminal charges. Legal consequences can include financial penalties, court proceedings, or damage to an individual’s or organization’s reputation. Moreover, violating an AUP can result in the loss of privileges, termination of employment, or legal action by affected parties. Understanding and adhering to the AUP is essential to avoid these potential legal ramifications.
AUP in Different Sectors
Usage of AUP in Corporate Sectors
AUPs are widely used in corporate sectors to govern the use of IT resources within organizations. They help protect sensitive company information, prevent security breaches, and address employee responsibilities and obligations. AUPs in corporate sectors often include guidelines on email communication, internet usage, remote access, social media, and the handling of intellectual property. By implementing AUPs, organizations can create a secure digital environment and minimize the risk of cyber threats.
Role of AUP in Educational Institutions
Educational institutions also rely on AUPs to ensure a safe and productive learning environment. AUPs in educational institutions set guidelines for technology use by students, teachers, and administrative staff. They address responsible internet browsing, email usage, online communication, and the use of school-provided devices. AUPs in educational institutions play a vital role in educating users about digital citizenship, fostering responsible online behavior, and protecting students and staff from cyber risks.
AUP in Mobile and Wireless Security
Challenges of Implementing AUP in a Mobile Environment
Implementing AUP in a mobile environment poses unique challenges. The proliferation of mobile devices and the prevalence of remote work make it difficult to monitor and enforce AUP compliance consistently. Additionally, the dynamic nature of mobile technology requires constant updates to AUPs to address emerging threats and vulnerabilities. Organizations face the challenge of ensuring that AUPs remain relevant and effective in the rapidly evolving mobile landscape.
Importance of AUP in Protecting Wireless Networks
Wireless networks are particularly vulnerable to security threats, making the presence of AUPs critical in protecting them. AUPs provide guidelines for secure wireless network usage, such as enforcing strong passwords, regular network monitoring, and restricting unauthorized access. Following AUP guidelines helps organizations protect their wireless networks from unauthorized intrusions, data breaches, and other security incidents.
Future of AUP in Cyber Security

Evolution of AUP with Technological Advancements
As technology continues to advance, AUPs will need to evolve to address new cyber threats and emerging technologies. The future of AUP lies in incorporating provisions for emerging trends, such as cloud computing, Internet of Things (IoT), and artificial intelligence (AI). AUPs will need to adapt to changing work environments, including remote work and the use of personal mobile devices, ensuring that security measures remain effective and relevant in the face of evolving cyber risks.
Predicted Changes in AUP Implementation and Enforcement
The implementation and enforcement of AUPs are likely to undergo changes in the future. Organizations may rely more on advanced technologies, such as artificial intelligence and machine learning, to monitor and enforce compliance. Additionally, there may be a greater emphasis on continuous security training and education to ensure that users are aware of the evolving cyber threats and their responsibilities under the AUP. Collaboration between organizations, industry forums, and regulatory bodies may also play a larger role in setting industry standards for AUP implementation and enforcement.
In conclusion, AUPs play a vital role in ensuring cyber security across different sectors. By setting clear guidelines for acceptable technology use, AUPs help organizations control user behavior, reduce security risks, and comply with legal requirements. As technology continues to evolve, AUPs must adapt to address emerging threats and changing work environments. Implementing and enforcing comprehensive AUPs is crucial in creating a secure digital environment and safeguarding against cyber threats.


Wow, after reading that article, I’m still not sure what AUP stands for! 🤔
“Who knew AUP could be so intriguing? Cyber security just got a whole lot more interesting!”
“Who needs AUP anyways? I say let the hackers roam free and have some fun!”
“LOL, who even reads those AUPs? Waste of time or essential for cyber security?”
Are you serious? Ignoring the AUP is like leaving your front door unlocked and expecting no one to break in. It’s not a waste of time, it’s common sense. Take responsibility for your own cyber security and stop whining about it.
I’ve read the article and I gotta say, AUP in Cyber Security sounds like alphabet soup to me! 🥣 Who’s with me?
I mean, who even needs to understand AUP in cyber security? Seems like a waste of time, if you ask me.
Wow, I couldn’t disagree more. Understanding AUP is vital in cyber security. It sets guidelines for responsible online behavior and protects both individuals and organizations from potential threats. Neglecting it is like leaving your front door wide open and hoping for the best. Don’t underestimate its importance.