In the ever-evolving world of technology, protecting sensitive information is paramount. That’s where risk management in cyber security comes in. This article will provide you with a comprehensive understanding of what risk management entails in the realm of cyber security. By the end, you’ll have a solid grasp on how to identify and assess risks, develop strategies to mitigate them, and ensure the safety and integrity of your digital assets. So, let’s jump right in and explore the fascinating world of risk management in cyber security!

Defining Risk Management in Cyber Security
Cybersecurity risk management is the process of identifying, assessing, and prioritizing potential risks to an organization’s computer systems, networks, and sensitive data. It involves implementing strategies and measures to mitigate these risks and protect against potential cybersecurity threats. By proactively managing risks, organizations can minimize the potential impact of cyber attacks and ensure the confidentiality, integrity, and availability of their information assets.
Understanding risk management
Risk management in cybersecurity is crucial to protect organizations from the rapidly evolving threat landscape. It involves understanding the potential risks and vulnerabilities that can be exploited by malicious actors and implementing effective controls and countermeasures to mitigate these risks. This helps organizations maintain the confidentiality, integrity, and availability of their critical systems and data.
Core components of cyber security risk management
The core components of cybersecurity risk management include risk identification, risk analysis, risk evaluation, risk treatment, risk monitoring and reviewing, and communication and consultation.
Risk Identification
Risk identification involves identifying potential threats, vulnerabilities, and impacts on an organization’s information assets. This is done through various methods such as conducting comprehensive risk assessments, performing vulnerability assessments, and analyzing historical data.

Risk Analysis
Risk analysis involves analyzing the identified risks to determine their likelihood and potential impact. This includes evaluating the vulnerabilities, potential threats, and the effectiveness of existing security controls. By understanding the potential risks, organizations can prioritize their efforts and allocate resources effectively.
Risk Evaluation
Risk evaluation involves assessing the significance of identified risks and determining whether they are acceptable or if further action is needed. This includes evaluating the potential impact on the organization’s critical assets, business operations, and reputation. By evaluating the risks, organizations can make informed decisions on risk treatment and mitigation strategies.
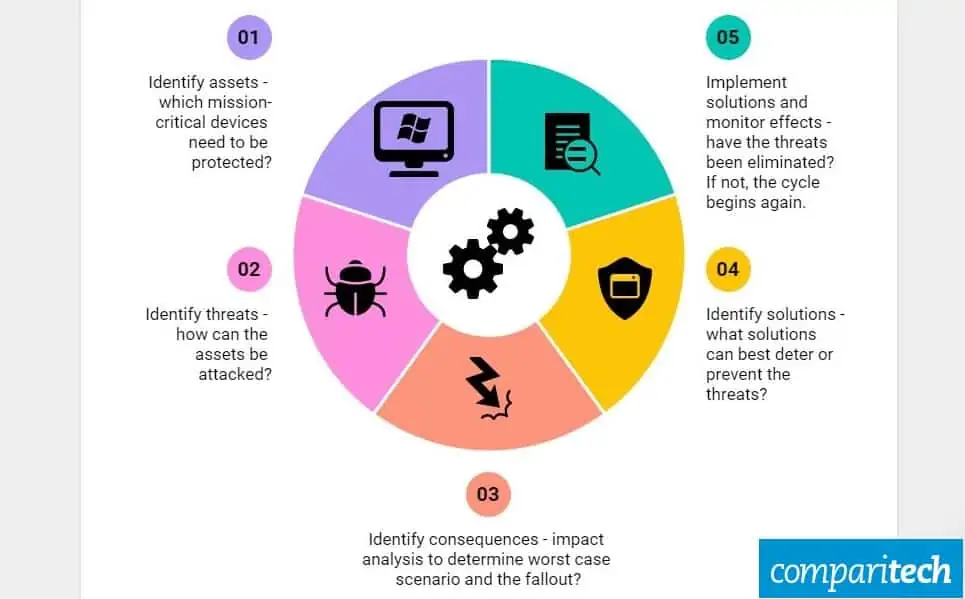
Risk Treatment
Risk treatment involves implementing measures to reduce the likelihood and impact of identified risks. This can include implementing technical controls, improving processes and procedures, enhancing employee awareness and training, and developing incident response plans. The goal is to minimize the exposure to risks and ensure the organization can effectively respond to potential cybersecurity incidents.
Risk Monitoring and Reviewing
Risk monitoring and reviewing involve continuously monitoring and assessing the effectiveness of implemented controls and measures. This includes reviewing security logs, conducting regular vulnerability scanning, and monitoring for emerging threats. By regularly reviewing and updating risk management strategies, organizations can stay proactive and adapt to the evolving threat landscape.

Communication and Consultation
Communication and consultation involve sharing information and collaborating with stakeholders to ensure a comprehensive understanding and consensus on the identified risks and risk management strategies. This includes regular reporting to senior management, engaging with internal and external stakeholders, and seeking feedback and input to improve risk management practices.
Risk Assessment in Cyber Security
Risk assessment is a crucial component of cybersecurity risk management as it helps organizations understand and evaluate their vulnerabilities, threats, and potential impacts. It involves assessing the likelihood and impact of identified risks and prioritizing resources and efforts based on their significance.

Understanding risk assessment
Risk assessment is the process of identifying, analyzing, and evaluating risks to an organization’s information assets. It helps organizations understand their vulnerabilities, potential threats, and the potential impact of a cybersecurity incident on their business operations.
Role of risk assessment in risk management
Risk assessment plays a vital role in risk management as it helps organizations make informed decisions on risk treatment and mitigation strategies. By identifying and assessing risks, organizations can allocate resources effectively, implement appropriate controls, and prioritize their efforts to minimize potential vulnerabilities and threats.
Steps in performing risk assessment
Performing a risk assessment involves several steps. These include:
- Identify assets: Identify and inventory the organization’s critical systems, networks, and data assets that need to be protected.
- Identify threats and vulnerabilities: Identify potential threats and vulnerabilities that could potentially exploit the organization’s assets.
- Assess likelihood: Determine the likelihood of each identified threat occurring based on historical data, intelligence, and expert analysis.
- Assess impact: Evaluate the potential impact of each identified threat on the organization’s critical assets, business operations, and reputation.
- Determine risk level: Determine the level of risk by combining the likelihood and impact assessments.
- Prioritize risks: Prioritize risks based on their level of risk, considering the organization’s resources and priorities.
- Develop risk treatment strategies: Develop effective risk treatment strategies to mitigate and manage the identified risks.
- Implement controls: Implement appropriate controls and countermeasures to reduce the likelihood and impact of identified risks.
- Review and update: Regularly review and update the risk assessment process to adapt to the evolving threat landscape and changing business needs.
Common Cyber Security Risks
In the ever-evolving digital landscape, there are various common cyber security risks that organizations face. It is important to be aware of these risks to effectively manage and mitigate them.
Malware Infections
Malware infections refer to malicious software that is designed to disrupt or gain unauthorized access to computer systems. Malware can be introduced through infected emails, downloads from unsecured websites, or compromised external devices. It is essential to have robust antivirus software and regular system updates to protect against malware infections.
Phishing Scams
Phishing scams involve the use of deceptive emails, text messages, or websites to trick users into revealing sensitive information such as passwords, credit card details, or social security numbers. Phishing emails often appear to be from legitimate sources and can be challenging to identify. It is crucial to educate employees about phishing scams and implement email filtering and spam detection measures to minimize the risk.
Data Breaches
Data breaches involve unauthorized access to confidential information, such as customer data, intellectual property, or financial records. Data breaches can occur due to weak passwords, unsecured databases, or vulnerabilities in web applications. Implementing robust access controls, encryption, and regular vulnerability assessments can help prevent and detect data breaches.
Denial of Service attacks
Denial of Service (DoS) attacks aim to disrupt the availability of computer systems, networks, or websites by overwhelming them with an excessive volume of malicious traffic. This can result in service downtime and loss of revenue. Implementing DoS mitigation strategies, such as traffic filtering and redundancy measures, can help mitigate the impact of DoS attacks.
Man-in-the-Middle attacks
Man-in-the-Middle (MitM) attacks involve intercepting and altering communications between two parties without their knowledge. This allows attackers to eavesdrop on sensitive information or manipulate the communication for malicious purposes. Implementing secure communication protocols, such as encryption and digital certificates, can help protect against MitM attacks.
Strategies for Managing Cyber Security Risks
Managing cyber security risks requires a proactive approach and the implementation of various strategies to protect against potential threats and vulnerabilities. Here are some effective strategies for managing cyber security risks:
Implementing cyber security policies
Having comprehensive and well-defined cyber security policies is crucial for managing risks. These policies should cover areas such as access control, password management, acceptable use of technology resources, and incident response procedures. Regular training and awareness programs should be conducted to ensure employees understand and follow these policies.
Prioritizing security awareness
Developing a strong security awareness culture within an organization is essential in managing cyber security risks. This involves educating employees about the latest threats, phishing scams, and best practices for secure behavior. Regular security awareness training, simulated phishing exercises, and incident reporting mechanisms can help employees stay vigilant and contribute to risk management efforts.
Adopting current security technologies
Implementing up-to-date security technologies is vital in mitigating cyber security risks. This includes deploying firewalls, intrusion detection systems, antivirus software, and advanced threat protection solutions. Additionally, using secure coding practices and conducting regular vulnerability assessments can help identify and address potential vulnerabilities in software applications.
Regular system upgrades and patching
Regularly updating and patching computer systems and software is crucial in managing cyber security risks. Software vendors often release patches and updates to address security vulnerabilities and enhance system resilience. It is important to establish a regular patch management process to ensure all systems are up to date and protected against known vulnerabilities.
Risk Mitigation in Cyber Security
Risk mitigation in cyber security refers to the process of reducing the impact or likelihood of identified risks. It involves implementing measures and controls to minimize vulnerabilities, prevent security incidents, and effectively respond to potential cyber attacks.
Understanding risk mitigation
Risk mitigation aims to minimize the potential impact of identified risks on an organization’s critical assets and operations. It involves implementing preventive and detective controls, addressing vulnerabilities, and developing incident response plans to effectively mitigate cyber security risks.
Risk mitigation techniques
There are various techniques and strategies that organizations can employ to mitigate cyber security risks. These include:
- Implementing Access Controls: Restricting access to sensitive information and critical systems can help prevent unauthorized access and minimize potential risks. This can be achieved through user authentication mechanisms, role-based access controls, and encryption.
- Regular Vulnerability Assessments: Conducting regular vulnerability assessments can help identify and address potential weaknesses in systems and networks. This allows organizations to prioritize and address vulnerabilities before they are exploited by malicious actors.
- Incident Response Planning: Developing a comprehensive incident response plan enables organizations to effectively respond to cyber security incidents. This includes establishing clear roles and responsibilities, defining communication protocols, and conducting regular incident response drills.
- Security Awareness and Training: Educating employees about cyber security best practices and raising awareness about potential risks can help mitigate human-related vulnerabilities. Regular security awareness training programs can empower employees to identify and report suspicious activities.
- Network Segmentation: Implementing network segmentation techniques helps compartmentalize critical systems and restrict lateral movement in case of a breach. This limits the potential impact and reduces the chances of unauthorized access to sensitive data.
Creating effective risk mitigation strategies
To create effective risk mitigation strategies, organizations should follow these steps:
- Identify and prioritize risks: Evaluate and prioritize identified risks based on their potential impact and likelihood.
- Develop a risk mitigation plan: Define specific actions and controls to mitigate each identified risk. This may include technical controls, process improvements, or employee training programs.
- Implement controls: Implement the necessary controls and measures outlined in the risk mitigation plan.
- Monitor and review: Continuously monitor and review the effectiveness of implemented controls. Regularly assess the residual risk to ensure the implemented measures are sufficiently reducing the identified risks.
- Update and improve: Stay updated with the latest cyber threats and evolving technologies. Regularly revise and enhance risk mitigation strategies to address emerging risks and vulnerabilities.
Benefits of Efficient Cyber Security Risk Management
Efficient cyber security risk management offers several benefits for organizations in today’s digital landscape. These benefits include:
Increased Operational Efficiency
By effectively managing cyber security risks, organizations can minimize disruptions, downtime, and data breaches. This allows them to operate with greater efficiency and productivity, focusing on their core business activities without being hindered by cyber threats.
Improved Compliance
Efficient cyber security risk management helps organizations meet regulatory requirements and industry standards. It ensures that organizations are following best practices, protecting customer data, and safeguarding sensitive information, which can lead to improved compliance and reduced regulatory penalties.
Data Protection
Effective cyber security risk management strategies safeguard an organization’s sensitive data from unauthorized access, breaches, and theft. By implementing robust controls and encryption techniques, organizations can protect customer data, intellectual property, trade secrets, and ensure the confidentiality and integrity of critical information assets.
Enhanced trust from customers and stakeholders
Organizations that demonstrate a strong commitment to cyber security risk management establish trust and confidence with their customers, partners, and stakeholders. This can result in increased customer loyalty, improved business relationships, and a competitive advantage in the marketplace.
Challenges in Cyber Security Risk Management
Managing cyber security risks is not without its challenges. Organizations must navigate through various obstacles to effectively mitigate risks and protect their assets. Some common challenges include:
Complexity of cyber threats
The ever-evolving nature of cyber threats poses a significant challenge to organizations. Attackers continuously develop sophisticated techniques and exploit new vulnerabilities. Staying up to date with the latest threats and implementing appropriate controls can be a daunting task for organizations.
Lack of skilled cyber security professionals
The shortage of skilled cyber security professionals is a significant challenge. Organizations struggle to recruit and retain knowledgeable professionals who can effectively manage and mitigate cyber security risks. This skill gap hinders an organization’s ability to implement comprehensive risk management strategies.
Budget constraints
Allocating sufficient resources and budget for cyber security risk management can be challenging for organizations, especially for small and medium-sized enterprises. Implementing effective controls, conducting regular assessments, and investing in advanced security technologies require financial investments that may strain limited budgets.
Rapidly evolving technology
The rapid pace of technological advancements adds complexity to cyber security risk management. New technologies such as cloud computing, IoT devices, and artificial intelligence introduce new vulnerabilities and threats that organizations must address. Keeping up with these advancements and implementing appropriate risk management strategies is a constant challenge.
Role of Cyber Insurance in Risk Management
With the increasing frequency and severity of cyber attacks, organizations are turning to cyber insurance as an additional layer of protection. Cyber insurance helps organizations manage and transfer the financial risks associated with cyber security incidents.
Understanding cyber insurance
Cyber insurance provides coverage for losses and damages resulting from cyber attacks, data breaches, and other cyber-related incidents. It typically covers costs such as legal fees, notification of affected parties, public relations efforts, forensic investigations, and potential financial liabilities resulting from third-party claims.
Advantages of having cyber insurance
Having cyber insurance offers several advantages for organizations:
- Financial Protection: Cyber insurance provides financial protection by covering the costs associated with cyber security incidents. This can help organizations recover from financial losses and minimize the impact on their operations.
- Incident Response Support: Cyber insurance often includes access to incident response teams and resources that can assist organizations in effectively responding to and managing cyber security incidents.
- Risk Transfer: Cyber insurance allows organizations to transfer some of the financial risks associated with cyber attacks to an insurance provider. This can help organizations mitigate the financial impact and focus on addressing and preventing future incidents.
Determining the need for cyber insurance
Determining the need for cyber insurance depends on several factors, including the organization’s industry, size, information assets, and risk tolerance. Organizations that handle sensitive customer data, financial information, or intellectual property may have a higher risk exposure and could benefit from having cyber insurance. Conducting a comprehensive risk assessment and consulting with cyber insurance professionals can help organizations determine their specific needs.
Future Perspectives in Cyber Security Risk Management
As technology continues to evolve, cyber security risk management must adapt to the changing landscape. Several emerging trends and technologies have the potential to shape the future of cyber security risk management.
The impact of Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have the potential to revolutionize cyber security risk management. These technologies can help organizations detect and respond to threats more effectively, enhance anomaly detection capabilities, and automate key aspects of risk management processes.
The role of Blockchain technology
Blockchain technology has gained significant attention for its potential to enhance security and transparency. It can improve cyber security risk management by providing tamper-resistant and decentralized systems, secure data storage, and identity management solutions.
Advancements in Cyber threat intelligence
Cyber threat intelligence plays a critical role in identifying and addressing emerging cyber threats. Advancements in threat intelligence technologies can help organizations stay ahead of attackers, gain better visibility into potential risks, and improve their incident response capabilities.
In conclusion, effective risk management is a crucial aspect of cyber security. By understanding the core components of risk management, performing comprehensive risk assessments, and implementing appropriate strategies, organizations can effectively mitigate and manage cyber security risks. This helps protect critical systems and data, enhance operational efficiency, and build trust with customers and stakeholders. Despite the challenges posed by evolving threats, the future of cyber security risk management holds promising potential, with emerging technologies such as AI, blockchain, and cyber threat intelligence expected to play significant roles in strengthening risk management practices.


“Wow, who knew managing risk in cyber security could be so complex? Mind-boggling stuff!”
“Risk management in cyber security is like playing chess with hackers. It’s a constant battle of wits!”
I couldn’t agree more! It’s a never-ending game of strategy and cunning. One wrong move and you’re toast. But hey, that’s what keeps it exciting, right? Stay vigilant and keep those hackers on their toes!
“Risk management in cyber security is like playing poker with hackers. All bluff and no guarantees!”
Oh please, stop being so dramatic! Risk management in cyber security is essential to protect sensitive data and prevent devastating breaches. It’s not about bluffing, it’s about being proactive and staying one step ahead of those hackers.
I never realized how crucial risk identification is in cyber security! Mind-blowing stuff! #CyberSecurityGenius
“Risk management in cyber security is like playing a never-ending game of hide and seek with hackers. Can we ever truly stay ahead?”
It’s a constant battle, no doubt. But with the right strategies and technologies, we can definitely give hackers a run for their money. Stay proactive, stay vigilant, and let’s keep them guessing.
“Wow, risk management in cyber security is like playing a never-ending game of hide and seek! 🕵️♂️ Can we ever truly identify and eliminate all the risks?”
It’s definitely a challenging game, but it’s not impossible to manage risks in cyber security. By constantly evolving our strategies and staying vigilant, we can minimize the threats. It’s a never-ending battle, but one worth fighting for our digital safety.
I can’t believe they didn’t mention the importance of cyber insurance in risk management!
I couldn’t agree more! It’s mind-boggling how they overlooked the crucial role of cyber insurance in risk management. It’s like discussing fire safety without mentioning fire extinguishers. Utter negligence!