Nowadays, VLANs have been cataloged as a very powerful way to manage medium and large local area networks.
Surely at some point, you’ve heard of them, but do not know very well what they are for and what advantages they offer in terms of security of communications, so it is useful when we want to segment the teams and limit access between them for security issues.
VLANs (Virtual Local Area Network), consists of two or more computer networks that behave as if they were connected to the same computer, although they are physically connected to different segments of a local area network, that is, an administrator can have several VLANs within the same router, grouping the computers of a particular network segment.
The main types of VLANs consist of static and dynamic, with static VLANs being those that are manually configured by assigning ports to a VLAN, and dynamic VLANs using a database that stores a VLAN-to-MAC mapping to determine the VLAN to which a particular host is connected, allowing hosts to move within the network instead of static networks.
Configuring the VMPS server that contains the VLAN-to-MAC mapping requires a lot of upfront work, so network administrators tend to prefer static VLANs.
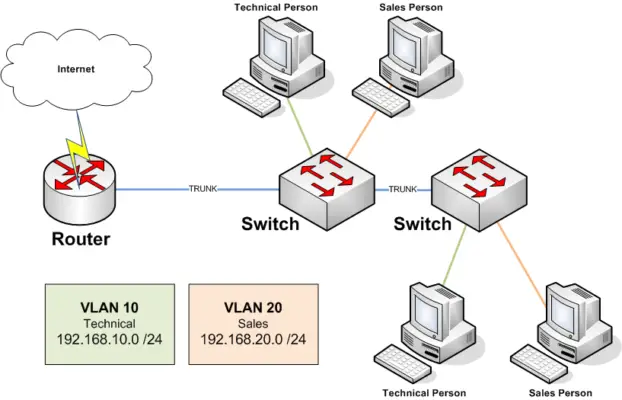
To further contextualize this concept, we can use the example of the actions of a company with several departments in which we want them to be independent, as they cannot exchange data over the network.
The solution would be to use several switches, one per department, or to use a switch logically divided into small switches, that is precisely a VLAN.
Then you need to generate access to services such as the internet and different servers, so you can:
Use a layer 3 and 4 switches or switch, that is, with the ability to “route” the different VLANs to a port.
Or use a firewall with VLAN support, that is to say, that in the same physical interface that works with several VLANs as if it had several physical interfaces.
Types of VLANs
VLANs can be classified according to the level of the OSI model:
Layer 1 VLAN
Defines a virtual network according to the switch port used, also known as “port switching”, is the most common and is implemented by most switches on the market.
Layer 2 VLAN
Defines a virtual network according to the MAC addresses of the computers. Compared to per-port VLAN, it has the advantage that computers can switch ports, but all MAC addresses must be assigned one by one.
Layer 3 VLANs
There are different types of Layer 3 VLANs, within this are:
- Network address-based VLAN connects subnets based on the IP address of the computers.
- Protocol-based VLAN, allows you to create a virtual network by type of protocol used.
The main difference is that VLAN is based on network address, having to parse packets to identify IP has slightly lower performance than protocol VLAN.
How does a per-port VLAN work?
The IEEE 802.1Q protocol handles the tagging of frames that are immediately associated with VLAN information.
VLAN “tagging”, is divided into two:
Untagged: since not all network cards offer the possibility to work with VLAN tags, the solution of most switch manufacturers, is to configure the ports as Untagged, i.e., untagged.
When a packet arrives at an UNTAGGED port, the switch is responsible for adding the “tag” to incoming frames and removing it from outgoing frames.
Tagged: When the device is connected, it can work directly with VLAN, it will send the information of the VLAN to which the device belongs. Thanks to this feature, the same port can work with several VLANs simultaneously.
When a port is configured with all the VLANs configured in TAGGED, it is cataloged as a Trunk. This system allows the packets of a VLAN to pass from one switch to another until all the devices of that VLAN are found.
The main advantages of segmenting your network using VLANs are as follows:
● Increases security.
By segmenting the network, groups that have sensitive data are separated from the rest of the network, decreasing breaches of confidential information.
● Improves performance.
By reducing and controlling the transmission of traffic on the network by dividing it into broadcast domains, performance is boosted.
● Reduces costs
There is little need for expensive network upgrades, as well as efficient uses of existing links and bandwidth.
It generates greater IT staff efficiency.
The VLAN defines a new network on top of the physical network, and by managing the network in a logical way, greater flexibility in network administration and changes is achieved, as the architecture can be changed using switch parameters, being able to: Move, add and configure workstations on the LAN.
In case of opting for a firewall with VLAN support, we can add the following advantages:
● Greater cost savings.
We will not have to invest in a switch with “routing capability”.
● Security and control.
We do not “route” one VLAN to another without any control, being able to create access rules between VLANs and inspect all traffic.
● Network performance.
We will have the possibility of prioritizing by QoS (Quality of Service) certain VLANs or protocols.
A clear example would be to prioritize Voice over IP (VoIP) traffic, as it requires:
- Bandwidth, to ensure voice quality.
- Priority of the transmission over other types of network traffic
- Ability to be routed in congested areas of the network
- Delay of less than 150 milliseconds (ms) across the network
Currently, having a Firewall with VLAN support means a number of important advantages when managing your information systems, where you will not only get performance improvements but also simplify your administration tasks will allowing you to learn new aspects and deepen the configuration of VLANs within your company.
