In the realm of cyber security, there lurks a growing threat known as skimming. This deceptive practice aims to exploit individuals’ vulnerable financial information by cleverly extracting data from unsuspecting victims. Skimming in cyber security refers to the act of stealing credit card details, PIN numbers, and other personal information by placing ingenious devices on payment terminals or ATM machines. By being aware of this nefarious technique and learning how to protect yourself, you can safeguard your finances and avoid falling victim to these covert attacks.
Understanding Skimming in Cybersecurity
Skimming is a prevalent attack method used by cybercriminals to illicitly obtain sensitive information, particularly financial data, from unsuspecting victims. In simple terms, skimming in cybersecurity refers to the act of stealing data, such as credit card numbers or personal identification information, directly from a payment card or a device used for financial transactions. This illicit activity has evolved over time and has become a significant threat in the digital landscape. By understanding the definition, history, types, mechanics, signs, impact, prevalence, prevention, dealing with attacks, case studies, and future trends of skimming attacks, individuals and businesses can better protect themselves against this form of cybercrime.
Definition of Skimming
In cybersecurity, skimming refers to the act of illegally obtaining data from a payment card or financial device for fraudulent purposes. Cybercriminals employ various techniques to capture sensitive information, including credit card numbers, PINs, and personal identification information, which can then be used to commit financial fraud. Skimming attacks can occur in both physical and digital forms, with criminals deploying sophisticated tactics to extract data without the victim’s knowledge or consent.
History of Skimming as an Attack Method
Skimming has a long history as an attack method in the realm of cybersecurity. The first recorded instances of skimming attacks date back to the 1980s when criminals began tampering with payment card devices and ATMs. Initially, skimming attacks were relatively simplistic, with criminals attaching physical devices to card readers to capture the magnetic stripe information. However, as technology advanced, skimming techniques evolved, and cybercriminals started leveraging digital methods to extract data remotely. This history highlights the constant evolution of skimming attacks and the need for continuous vigilance against this form of cybercrime.
Types of Skimming
Skimming attacks can be categorized into several types, each targeting specific areas in the realm of financial transactions. Understanding these various types of skimming is crucial for identifying potential threats and implementing effective countermeasures.
Credit Card Skimming
Credit card skimming involves the unauthorized capture of data directly from credit cards during point-of-sale transactions. Criminals often tamper with the card reader devices or use hidden cameras to record PIN entries. This stolen data can then be used to create cloned credit cards or make fraudulent purchases.
ATM Skimming
ATM skimming occurs when cybercriminals tamper with the card slot or PIN pad of an automated teller machine (ATM) to gather card information and personal identification numbers. Skimming devices installed on the ATM can read the magnetic stripe on the card or capture keystrokes, allowing criminals to gain access to the victims’ bank accounts.
Data Skimming
Data skimming, also known as web skimming or form jacking, targets online payment platforms or e-commerce websites. Cybercriminals inject malicious code into legitimate websites or create fake websites that mimic legitimate ones. When victims input their payment information, the skimming code captures the data and sends it to the attacker, enabling fraudulent activities.

Mechanics of Skimming Attacks
Understanding how skimming attacks work is essential for identifying potential threats and taking adequate measures to prevent them. By exploring the mechanics of skimming attacks, individuals and businesses can better protect themselves against this form of cybercrime.
How Skimming Devices Work
In physical skimming attacks, criminals typically install skimming devices on payment card terminals, ATMs, or other electronic point-of-sale systems. These devices are designed to capture the information encoded on the card’s magnetic stripe or the keystrokes entered on a PIN pad. Skimming devices can be relatively small and discreet, making them difficult to detect. Once the victim uses the compromised device, the skimming device collects the data, which the criminals can later retrieve.
Offline Versus Online Skimming
Skimming attacks can be classified as either offline or online skimming, depending on how the stolen data is used. Offline skimming involves the extraction of data from the compromised device itself. The criminals physically retrieve the skimming device and access the captured data stored within it. In contrast, online skimming involves the captured data being transmitted in real-time to the attackers. This data is then used to clone credit cards or conduct immediate fraudulent transactions.
Physical Vs. Digital Skimming
Skimming attacks can also be categorized as physical or digital, based on the medium through which the attack is executed. Physical skimming refers to the use of physical devices attached to payment card readers or ATMs to capture data. These devices can range from card skimmers to hidden cameras. On the other hand, digital skimming involves the injection of malicious code into websites, which captures payment information when victims make online transactions. This distinction emphasizes the versatility and diversity of skimming attack methods.
Signs of Skimming Attacks
Recognizing the signs of a skimming attack is crucial for taking prompt action and minimizing the potential damage. By being aware of the common indicators, individuals and businesses can protect themselves against falling victim to skimming attacks.
Sudden Unexplained Financial Transactions
One of the most significant signs of a skimming attack is the presence of unexplained financial transactions. This can include unauthorized purchases, withdrawals, or transfers from bank accounts or credit cards. If you notice unfamiliar transactions on your account statements, it may indicate that your financial information has been compromised through skimming.
Appearance of Strange Devices on ATMs
When using an ATM, be vigilant and pay attention to any unusual devices attached to the machine. Skimming devices are designed to blend in with the legitimate components of an ATM, making them difficult to spot. Look for anything that appears out of place, such as loose or misaligned card readers, extra attachments on the keypad, or suspicious cameras. If you suspect skimming, it is best to avoid using the ATM and report it to the relevant authorities.
Noticeable Changes in Website Interface or Behavior
For online transactions, it is crucial to stay vigilant and monitor any changes in website interfaces or behavior. Skimming attacks that target online payment platforms or e-commerce websites often involve the injection of malicious code. If you notice sudden alterations in the appearance or functionality of a website during the payment process, it may indicate the presence of skimming malware. In such cases, refrain from entering your payment information and report the incident to the website operator.

Impact of Skimming
Skimming attacks can have significant consequences for both individuals and businesses. Understanding the impact of skimming is crucial for raising awareness and implementing appropriate measures to mitigate the risk.
Financial Losses Due to Skimming
The most immediate and apparent impact of skimming attacks is financial loss. Victims of skimming attacks may find unauthorized transactions draining their bank accounts, resulting in significant financial setbacks. Credit card fraud can also lead to substantial financial burdens for both individuals and businesses, requiring substantial effort and expense to resolve.
Trust and Reputation Damage for Businesses
For businesses, falling victim to a skimming attack can severely damage their trust and reputation. Customers who have their data compromised through skimming attacks may lose confidence in the business’s ability to protect their information, resulting in a loss of trust. This can have long-term negative impacts on customer loyalty, brand reputation, and ultimately, the overall success of the business.
Breach of Privacy for Individuals
Skimming attacks can result in a significant breach of privacy for individuals. The stolen data may include personal identification information, such as names, addresses, and even social security numbers. When this information falls into the wrong hands, it can be used for further identity theft or other malicious activities, leading to potential harm and inconvenience for the victims.
Prevalence of Skimming
Skimming attacks have become increasingly prevalent in recent years, affecting individuals and businesses worldwide. Understanding the global statistics and industries most affected by skimming can help individuals and organizations recognize the importance of implementing preventive measures.
Global Statistics on Skimming Attacks
Skimming attacks have become a global concern, with cybercriminals targeting various countries across the world. Recent statistics have shown a significant rise in skimming incidents, with millions of dollars being stolen annually. These attacks affect individuals from all walks of life, making it crucial for everyone to remain vigilant and take proactive measures to prevent falling victim to skimming.
Industries Most Affected By Skimming
While skimming attacks can occur across various industries, some sectors are more frequently targeted than others. Retail, hospitality, and banking are particularly vulnerable to skimming attacks due to the prevalence of payment card transactions. These industries often handle a large volume of customer transactions daily, providing ample opportunities for criminals to tamper with payment devices or inject malicious code into websites.
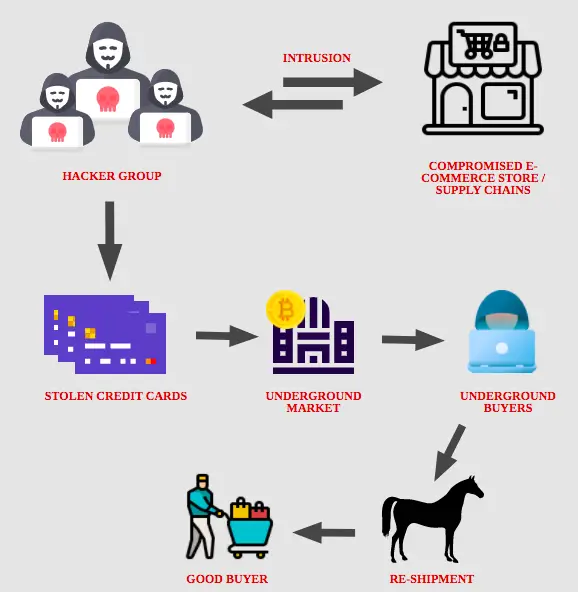
Preventing Skimming
The prevention of skimming attacks is crucial for safeguarding personal and financial information. By implementing best practices and utilizing technologies designed to prevent skimming, individuals and businesses can significantly reduce the risk of falling victim to this form of cybercrime.
Best Practices for Individuals
Individuals can take several precautionary measures to protect themselves from skimming attacks. First and foremost, it is essential to be cautious when using payment card terminals or ATMs. Inspect the devices for any signs of tampering, such as loose components or hidden cameras, before conducting any transactions. Additionally, using secure online payment platforms and regularly monitoring bank and credit card statements can help detect any suspicious activities promptly. Lastly, staying informed about the latest skimming techniques and maintaining robust cybersecurity measures, such as strong passwords and up-to-date antivirus software, can provide an additional layer of protection.
Best Practices for Businesses
Businesses must prioritize skimming prevention to safeguard customer data and maintain trust. Regular inspections of payment terminals, ATMs, and other transaction devices can help identify any signs of tampering. Businesses should also educate their employees on skimming awareness and provide clear guidelines on the protocols to follow if skimming is suspected. Utilizing encryption technologies, secure payment gateways, and consistently updating software systems can further enhance the security infrastructure. Additionally, organizations must have robust incident response plans in place to minimize the impact of a successful skimming attack.
Technologies Designed to Prevent Skimming
Developers and security experts continue to innovate technologies designed to counter skimming attacks. Point-to-point encryption (P2PE) is one such technology that encrypts data from the moment it is entered into a payment device, rendering it useless to skimming criminals. Secure payment gateways also play a crucial role in preventing skimming by establishing secure channels for online transactions. Incorporating machine learning and artificial intelligence algorithms into security systems can aid in the early detection of skimming attempts, providing an additional layer of protection for individuals and businesses.
Dealing with Skimming Attacks
In the unfortunate event of a skimming attack, individuals and businesses must take immediate action to mitigate the damage and regain control. Understanding the steps to take after discovering a skimming attack, working with financial institutions, and reporting the incident to law enforcement can help minimize the impact and increase the chances of apprehending the criminals.
First Steps After Discovering a Skimming Attack
Upon discovering a skimming attack, the first step is to safeguard personal or financial information by changing relevant login credentials or PINs. Next, it is crucial to contact the financial institution involved, such as the bank or credit card provider, to report the incident and freeze affected accounts. By taking these initial steps promptly, individuals can minimize the financial loss and prevent further unauthorized transactions.
Working with Financial Institutions After a Skimming Attack
Cooperating and working closely with financial institutions is essential in resolving a skimming attack. Provide the necessary evidence, including transaction records and any relevant findings, to assist the investigation. Financial institutions can help in recovering stolen funds, reversing fraudulent transactions, and providing guidance on enhancing security measures. Regularly communicating with the financial institution throughout the recovery process is vital in restoring normalcy and preventing future incidents.
Reporting Skimming Attacks to Law Enforcement
Reporting skimming attacks to law enforcement agencies is crucial for raising awareness and aiding ongoing investigations. Contact local law enforcement or the appropriate cybercrime division to report the incident, providing all available evidence and details. By reporting skimming attacks, you contribute to the collective effort in combating cybercrime and increasing the chances of apprehending the perpetrators.

Case Studies of Skimming
Studying notable instances of skimming attacks can offer valuable insights and lessons for individuals and businesses. Examining past cases can shed light on the various techniques employed by cybercriminals and underscore the importance of staying vigilant against evolving skimming threats.
Notable Instances of Skimming Attacks
Several high-profile skimming attacks have made headlines over the years, showcasing the severity and sophistication of these cybercrimes. From large-scale data breaches affecting prominent retail chains to targeted attacks on financial institutions, these instances have led to substantial financial losses and reputational damage. Analyzing these cases can help individuals and businesses understand the tactics employed by cybercriminals and take necessary precautions.
Lessons Learned from Past Skimming Attacks
Past skimming attacks have taught valuable lessons regarding the importance of proactive prevention and diligent monitoring. The recurring theme of inadequate security measures leading to successful skimming attacks emphasizes the need for robust security practices by both individuals and organizations. Additionally, timely incident response, cooperation with law enforcement, and continuous improvement of security measures are crucial lessons that need to be implemented to prevent future skimming attacks.
Future of Skimming
As technology continues to evolve, skimming attacks are likely to adapt and become more sophisticated. Understanding the emerging skimming techniques, the evolving landscape of anti-skimming technology, and the role of government regulation in mitigating skimming can help individuals and businesses stay one step ahead in the ongoing battle against cybercrime.
Emerging Skimming Techniques
Cybercriminals are constantly exploring new techniques to carry out skimming attacks. The rise of contactless payment methods, such as digital wallets and near field communication (NFC), introduces new vulnerabilities that can be exploited. Additionally, advancements in artificial intelligence and machine learning may empower attackers to develop more stealthy and targeted skimming tactics. Staying informed about emerging skimming techniques is crucial for implementing effective countermeasures.
Evolving Anti-Skimming Technology
To counter the evolving threat of skimming attacks, technology developers are diligently working on innovative anti-skimming solutions. Enhanced encryption methods and tamper-evident devices are being designed to foil skimming attempts. Software solutions equipped with advanced algorithms and artificial intelligence capabilities can detect abnormal transaction patterns or suspicious website activities. By leveraging these evolving technologies, individuals and businesses can continue to strengthen their defenses against skimming attacks.
Role of Government Regulation in Mitigating Skimming
Governments and regulatory bodies have a critical role to play in mitigating the impact of skimming attacks. The implementation of robust cybersecurity regulations, data protection laws, and compliance standards can provide a solid foundation for preventing skimming. Governments can also enhance collaboration with law enforcement agencies, financial institutions, and private entities to share intelligence, develop advanced anti-skimming strategies, and prosecute cybercriminals effectively.
In conclusion, skimming attacks pose a significant threat in the realm of cybersecurity. Understanding the definition, history, types, mechanics, signs, impact, prevalence, prevention, dealing with attacks, case studies, and future trends of skimming is crucial in combating this form of cybercrime. By implementing best practices, utilizing advanced technologies, and collaborating with regulatory bodies and law enforcement agencies, individuals and businesses can fortify their defenses and protect themselves against the growing threat of skimming attacks. Stay informed, stay vigilant, and stay one step ahead of cybercriminals.


