In an increasingly digital world, it has become vital to understand the impact of cyber threats. With technology playing a central role in our daily lives, the risk of cyber-attacks and data breaches has never been higher. This article explores the consequences of cyber threats, shedding light on the potential harm they can cause to individuals, businesses, and society as a whole. From financial losses to compromised personal information, gaining a deeper understanding of these threats is crucial in safeguarding ourselves and our digital presence.
Defining Cyber Threats
Understanding the concept of cyber threats
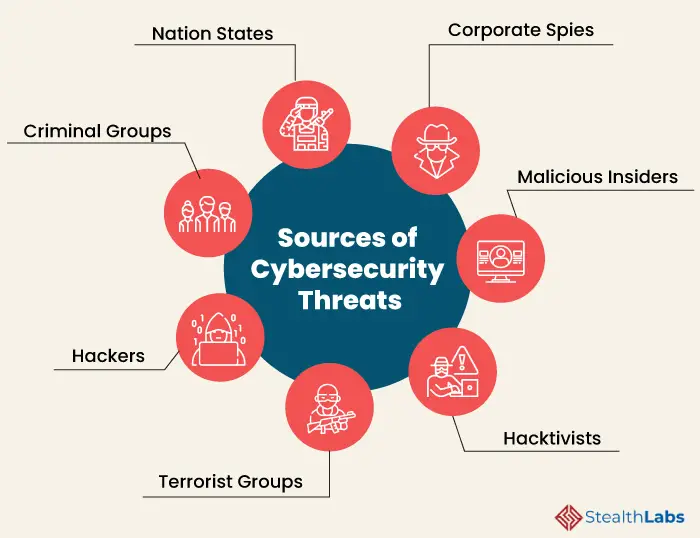
In today’s increasingly digital world, cyber threats have become a significant concern for individuals, businesses, and nations alike. Cyber threats refer to any malicious activities that target computer systems, networks, or users, with the intention of causing harm or gaining unauthorized access to sensitive information. These threats can take various forms, such as hacking, malware attacks, phishing scams, and distributed denial of service (DDoS) attacks. Understanding the concept of cyber threats is crucial in order to effectively protect ourselves and mitigate the risks they pose.
Different types of cyber threats
Cyber threats encompass a wide range of malicious activities that can be categorized into different types. One common type is hacking, where attackers exploit vulnerabilities in computer systems or networks to gain unauthorized access. Malware attacks involve the use of malicious software, such as viruses, worms, or ransomware, to disrupt or damage computer systems. Phishing attacks, on the other hand, trick users into providing sensitive information, such as passwords or credit card details, by posing as legitimate entities. Additionally, DDoS attacks overwhelm a target system or network with a flood of traffic, rendering it inaccessible. These are just a few examples of the many different types of cyber threats that individuals and organizations need to be aware of.
How cyber threats occur
Cyber threats can occur through a variety of avenues and techniques. One common method is through exploiting software vulnerabilities. Attackers often target outdated or insecure software to gain access to systems. Social engineering is another technique frequently employed by cybercriminals, as they manipulate individuals into revealing sensitive information or performing actions that compromise security. Phishing emails and phone scams are examples of social engineering tactics. Furthermore, cyber threats can occur through malicious downloads, drive-by downloads, or even physical tampering with computer systems. It is important to stay vigilant and be aware of these methods to prevent falling victim to cyber threats.
Understanding the World of Cybercrime
Rise in cybercrime trends
The world of cybercrime has witnessed a significant rise in recent years. With the increasing reliance on technology and the exponential growth of the internet, cybercriminals have found new avenues to exploit vulnerabilities and carry out their malicious activities. The availability of hacking tools and marketplaces on the dark web has further fueled the rise in cybercrime. Additionally, the COVID-19 pandemic has played a role in the surge of cybercrime, as attackers exploit fears and uncertainties to deceive individuals and organizations. It is crucial to understand these trends in order to effectively combat cybercrime.
The role of technology in facilitating cybercrime
Technology plays a pivotal role in facilitating cybercrime. Advancements in communication networks, computing power, and the widespread adoption of internet-connected devices have created a larger attack surface for cybercriminals to target. The interconnected nature of technology, known as the Internet of Things (IoT), has further expanded the potential vulnerabilities that can be exploited. Moreover, the increasing digitization of financial transactions and the storing of personal information online have provided cybercriminals with lucrative targets. It is essential to recognize the role of technology in cybercrime to develop effective security measures.
High-profile examples of cybercrime
Numerous high-profile cybercrime incidents have shaken the world in recent years, highlighting the severity of the issue. One notable example is the massive data breach that occurred in 2017, where Equifax, one of the largest credit reporting agencies in the United States, suffered a cyber attack that exposed the sensitive personal information of approximately 147 million individuals. Another significant incident was the WannaCry ransomware attack in 2017, which affected hundreds of thousands of computers worldwide, disrupting critical services, and caused financial losses. These high-profile examples illustrate the far-reaching impact and consequences of cybercrime.
Impacts of Cyber Threats on Personal Security
Personal data and identity theft
One of the most significant impacts of cyber threats on personal security is the risk of personal data and identity theft. Cybercriminals often target personal information, such as social security numbers, bank account details, and login credentials, to carry out fraudulent activities or sell the stolen data on the dark web. Identity theft can have devastating consequences, including financial loss, damage to credit history, and emotional distress. Protecting personal information and implementing strong security measures are essential to mitigate the risks of identity theft.
Financial loss due to cyber fraud
Cyber fraud is a major concern when it comes to the impact of cyber threats on personal security. Various forms of cyber fraud, such as online scams, phishing attacks, and credit card fraud, can result in significant financial losses for individuals. Cybercriminals employ deceptive tactics to trick individuals into providing sensitive financial information, which they then use to carry out fraudulent transactions or drain bank accounts. Being cautious and alert to potential fraud attempts is crucial to minimize the risk of financial loss.
Psychological consequences of cyber threats
In addition to the tangible impacts, cyber threats can also have psychological consequences on individuals. Falling victim to a cyber attack or experiencing a security breach can lead to feelings of violation, vulnerability, and mistrust. The fear of further attacks or the loss of privacy can create significant stress and anxiety. It is important to address these psychological consequences and provide support to individuals who have been affected by cyber threats.
Impact of Cyber Threats on Businesses
Economic costs to businesses
Cyber threats pose significant economic costs to businesses. The financial impact of cyber attacks includes direct costs, such as expenses related to investigating and mitigating the attack, restoring systems, and compensating affected individuals. Indirect costs, such as loss of customers, damage to reputation, and decreased productivity due to downtime, further exacerbate the economic impact. These costs can be crippling for small businesses and have a profound impact on the overall economy. Implementing robust cybersecurity measures is essential to minimize the economic burden of cyber threats.
Damage to brand reputation
The reputational damage caused by cyber threats is a major concern for businesses. When a company suffers a data breach or falls victim to a cyber attack, it erodes customer trust and confidence. The negative publicity and media attention surrounding such incidents can tarnish a brand’s reputation, leading to a loss of customers and a decrease in market share. Rebuilding a damaged reputation takes time and effort, making proactive cybersecurity measures crucial to safeguard brand reputation.
Disruption in business operations
Cyber threats can cause significant disruptions in business operations, leading to financial losses and decreased productivity. DDoS attacks, for example, can render websites and online services unavailable, resulting in lost sales and customer dissatisfaction. Ransomware attacks can encrypt critical data, preventing employees from accessing necessary information and bringing operations to a standstill. The downtime and costs associated with resolving these disruptions can be detrimental to businesses. Developing comprehensive incident response plans and regularly testing the resilience of systems can help minimize the impact of cyber threats on business operations.

Effects of Cyber Threats on National Security
Cyber threats and national defense
Cyber threats have become a major concern for national defense. State-sponsored cyber attacks and cyber espionage pose a significant threat to the security and sovereignty of nations. By infiltrating government networks and stealing sensitive information, attackers can compromise national security secrets, military strategies, and critical infrastructure systems. The potential disruption and damage caused by cyber attacks on national defense can have far-reaching consequences, making it essential for governments to prioritize robust cybersecurity measures and invest in cyber defense capabilities.
Cyber espionage and state secrets
Cyber espionage, conducted by both state-sponsored actors and independent hackers, involves the theft of sensitive information and technological advancements from other nations. This information can be used to gain a competitive advantage in various sectors, such as defense, technology, and finance. The theft of state secrets and intellectual property through cyber espionage undermines national security and can result in significant economic losses. Governments need to enhance their cybersecurity capabilities and establish effective mechanisms for deterring and responding to cyber espionage.
Impact on critical national infrastructure
Critical national infrastructure, such as power grids, transportation systems, and healthcare facilities, is highly dependent on technology and vulnerable to cyber threats. A successful cyber attack on these systems can have catastrophic consequences, affecting the safety, well-being, and resilience of a nation. Disrupting power grids, compromising transportation networks, or compromising healthcare systems can paralyze a country and put lives at risk. Strengthening the cybersecurity of critical national infrastructure and developing robust contingency plans are imperative to protect national security.
Impact of Cyber Threats on Societal Infrastructure
Effect on healthcare systems
Cyber threats can have devastating effects on healthcare systems, impacting patient care and compromising sensitive medical information. In recent years, there has been a surge in cyber attacks targeting healthcare organizations, primarily driven by the value of medical data on the black market. The disruption of healthcare systems can hinder access to critical services, delay treatments, and jeopardize patient safety. Safeguarding healthcare infrastructure and adopting stringent cybersecurity measures are essential to protect patient data and ensure the smooth functioning of healthcare services.
Impact on the education sector
The education sector is not immune to the impact of cyber threats. Educational institutions store vast amounts of personal information and research data, making them attractive targets for cybercriminals. Data breaches can result in the exposure of sensitive student information and intellectual property theft. Disruption of online learning platforms and educational systems can impede students’ access to quality education. It is crucial for educational institutions to prioritize cybersecurity and educate staff and students about best practices to mitigate cyber threats.
Disruption of public transportation systems
Public transportation systems are increasingly reliant on technology and interconnected networks, making them vulnerable to cyber threats. A successful cyber attack on transportation systems can disrupt schedules, compromise safety mechanisms, and compromise operations. Attackers can potentially manipulate traffic systems, disable train signaling, or compromise the security of airport control systems. The disruption of public transportation not only affects the daily lives of citizens but can also have severe economic and societal consequences. Enhancing the cybersecurity of transportation systems is critical to ensuring the safety and efficiency of public transportation.

Underlining the Global Impact of Cyber Threats
Emerging cyber threat landscapes
The global impact of cyber threats is further accentuated by the emergence of new cyber threat landscapes. As technology evolves and becomes more sophisticated, cybercriminals adapt their techniques to exploit emerging vulnerabilities. Emerging threats include the rise of ransomware as a service (RaaS), where attackers offer ransomware tools and support to non-technical individuals, as well as the increasing targeting of cloud services and Internet of Things (IoT) devices. Stayin updated on these evolving cyber threat landscapes is essential to effectively combat cyber threats.
Global economic impact
The global economic impact of cyber threats is staggering. The costs of cyber attacks and data breaches are estimated to reach trillions of dollars annually. These costs include financial losses, expenses related to incident response, and the long-term impact on businesses and economies. Small and medium-sized enterprises (SMEs) are particularly vulnerable, as they often lack the resources and expertise to effectively address cyber threats. Therefore, international cooperation and collaboration are crucial to minimize the global economic impact of cyber threats.
Interplay between geopolitics and cyber threats
Cyber threats are not isolated incidents but are influenced and shaped by geopolitics. Geopolitical tensions and conflicts between nations can spill over into cyberspace, where governments and state-sponsored actors engage in cyber warfare and cyber espionage. The use of cyber attacks as a tool for political coercion or sabotage is a growing concern. The interplay between geopolitics and cyber threats highlights the importance of international norms, treaties, and agreements to regulate and prevent cyber conflicts.
Mitigating the Impact of Cyber Threats
Security measures for personal protection
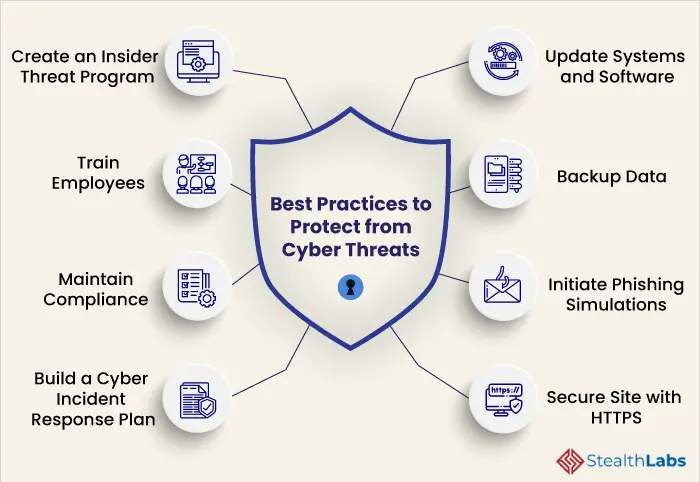
As individuals, there are several security measures we can take to protect ourselves from cyber threats. First and foremost, it is crucial to maintain strong and unique passwords for all online accounts and enable two-factor authentication whenever possible. Regularly updating software and operating systems, using reputable antivirus and anti-malware software, and being cautious when clicking on suspicious links or downloading files are also essential practices to ensure personal protection. Additionally, staying informed about the latest cyber threats and adopting safe online behaviors can significantly reduce the risk of falling victim to cyber attacks.
Business strategies for mitigating cyber risks
Businesses must adopt comprehensive strategies to mitigate the risks posed by cyber threats. This includes implementing robust cybersecurity protocols, such as firewalls, intrusion detection systems, and encryption techniques to protect data and network infrastructure. Regular employee training and awareness programs are essential to educate staff about cybersecurity best practices and potential threats. Developing an incident response plan and regularly testing the resilience of systems through simulated exercises are also crucial steps to minimize the impact of cyber threats on businesses.
National policies for cyber defense
Governments play a crucial role in mitigating the impact of cyber threats through the implementation of national policies for cyber defense. This includes establishing dedicated cybersecurity agencies or task forces, investing in research and development of advanced cybersecurity technologies, and fostering international cooperation to combat cybercrime and cyber terrorism. National policies should also focus on promoting cybersecurity education and awareness from an early age, ensuring that the next generation is equipped with the knowledge and skills to navigate the digital world securely.
Future of Cyber Threats and Its Potential Impact
Predicted cyber threats scenarios
The future of cyber threats is characterized by increasing sophistication and a growing number of potential attack vectors. As technology continues to evolve, cybercriminals will leverage artificial intelligence and machine learning to enhance their attack capabilities. Predicted cyber threats scenarios include AI-powered malware that adapts to its environment, attacks targeting emerging technologies such as autonomous vehicles and smart grids, and the use of quantum computing to break encryption. It is essential for individuals, businesses, and governments to anticipate and prepare for these future cyber threats.
Role of artificial intelligence and machine learning in cyber threats
Artificial intelligence and machine learning are powerful tools that both defenders and attackers can utilize in the realm of cyber threats. While AI and machine learning can enhance cybersecurity measures through the detection and mitigation of threats, they can also be leveraged by cybercriminals to automate attacks and evade detection. The arms race between defenders and attackers in the realm of AI and machine learning is likely to shape the future of cyber threats. It is imperative to invest in AI-driven cybersecurity technologies and develop robust defense mechanisms to stay ahead of cybercriminals.
Potential impact on the Internet of Things (IoT)
The rapid proliferation of internet-connected devices, collectively known as the Internet of Things (IoT), introduces a myriad of new cyber threats. With billions of devices interconnected, the potential attack surface for cybercriminals expands exponentially. Compromised IoT devices can be used as entry points into networks or harnessed as part of massive botnets for carrying out coordinated attacks. As the IoT ecosystem continues to grow and integrate with critical infrastructure, the potential impact of IoT-related cyber threats on society becomes increasingly significant. It is crucial to prioritize IoT security and implement robust measures to protect these interconnected devices.
Conclusion: Towards a Cyber-Resilient Future
In today’s increasingly digital world, cyber threats pose significant challenges to individuals, businesses, and nations. Understanding the concept of cyber threats, their different types, and how they occur is crucial in order to effectively protect ourselves and mitigate the risks they pose. The impacts of cyber threats on personal security, businesses, national security, and societal infrastructure are far-reaching and can have profound consequences. However, by implementing comprehensive security measures, adopting proactive strategies, and fostering international cooperation, we can work towards a cyber-resilient future. Creating a culture of cyber resilience, where individuals are educated about cybersecurity and organizations prioritize robust defense mechanisms, is essential in overcoming the ever-evolving cyber threats landscape. By learning from past incidents and staying abreast of emerging cyber threats, we can navigate the digital world securely and ensure a safer and more resilient future.

