After nearly two years of planning, the new UK Government Security Classification system comes into operation this month. This will probably be accompanied by some articles from the doomsday brigade suggesting forecasting chaos and uncertainty; there are undoubtedly rough edges, but it’s important not to lose sight of the bigger cultural change at play…
In summary, the current multi-layer model of TOP SECRET, SECRET, CONFIDENTIAL, RESTRICTED, PROTECT and UNCLASSIFIED collapses to three tiers of TOP SECRET, SECRET and OFFICIAL. But to see it as simply a re-labelling exercise misses the point of the change – and more crucially the opportunity.
The old system was implemented inconsistently, using a combination of policy, guidance and local procedures, with technology sitting separately. The new system relies on people making value judgements.
The scheme has been adopted on the auspices of reducing cost and providing clarity to public sector workers as to their data handling responsibilities, taking into account the requirements of the ‘information age’.
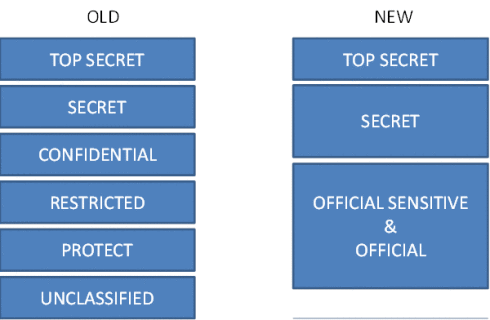
There are no direct mappings, hence no arrows.
Note: there is no longer an UNCLASSIFIED layer. If it is government data, it’s OFFICIAL (as a minimum – whether marked or unmarked) and must be treated as such. If it’s not government data, then it’s not covered by the Classification scheme.
Scope
The scope of the classification changes are wide, encompassing central government, defence, intelligence agencies, local and regional government, police and health. In addition, the industrial supply chain to public sector is expected to conform too. Although only direct government departments will be adopting this from 2nd April, others will follow and estimates puts the number at somewhere between 5-10 million UK citizens who will need to know what OFFICIAL means, and how to handle it appropriately.
For an interim period, both the old and new systems will need to be run in parallel.
With a scale of so many organisations and people who have never had to think in this way before, there bound to be rough edges!
Rough Edges
Confusion surrounds the marking OFFICIAL SENSITIVE.
- The Cabinet Office (creators of the policy) insist there are three tiers with OFFICIAL SENSITIVE being incorporated within the OFFICIAL tier and used to single the data out for extra-care when handling. It is hard to explain why this is not effectively the fourth tier – most people see it that way.
- Whereas the data itself is still OFFICIAL, the tools and techniques to protect OFFICIAL SENSITIVE can in principle be the same but treated with extra handling care as the impact of its loss is greater. This is not always true, as OFFICIAL SENSITIVE, for example, should be encrypted if sent over the Internet but this is not a requirement for OFFICIAL. Which makes it feel like a 4th tier with different needs?
- To add to the confusion the MoD Industry Security Notice 2014/01 all but defines this as a separate layer, in short saying that what was RESTRICTED to now treat as OFFICIAL SENSITIVE and carry on as before.
- To further add confusion, various systems at CONFIDENTIAL will remain in operation for an interim period while they are upgraded to SECRET or downgraded to OFFICIAL SENSITIVE.
- According to some documents, the concept of EU RESTRICTED will remain for companies dealing with European classified data, but handled as OFFICIAL SENSITIVE, again giving the feel of a separate 4th layer. However, there is some contradiction here too, suggesting that for this case the concept of a RESTRICTED system will remain.
Threat Models
Another significant change is the use of Business Impact Levels (BIL). According to the Cabinet Office FAQ
BILs have been widely misused beyond their intended purpose, which has led to significant negative outcomes” and “people have misused BIL value as a proxy for security requirements, often leading to assumptions of the security measures which are present in that system”, but maintain that “Reference by a security professional to the BIL tables remains acceptable in the course of a comprehensive risk assessment, provided that BILs should not be used to describe the security offered by an IT system.
That will be a big change – not least to PSN which uses BILs for exactly that purpose. The new threat model defined for OFFICIAL is worthy of note (Appendix A in the Cabinet Office FAQ):
For the generality of its business and to deliver services in a modern, accessible and cost-effective fashion, HMG needs to work in the same way as any large and well run UK commercial organisation. This means adopting a commercial threat model that protects information and services against attackers with bounded resources and capabilities, including hactivists, single-issue pressure groups, investigative journalists, competent individual hackers and most criminals.
HMG is satisfied that this model will mean, amongst other things, that the confidentiality of citizen data and routine commercial dealings is assured. This does not imply that OFFICIAL information will not be targeted by sophisticated and determined threats (including Foreign Intelligence Services) but a decision has been taken to manage these risks in order to ensure efficiencies and allow government organisations to operate effectively. This approach is underpinned by an understanding that the majority of information risks can be successfully managed by getting the basics right: good governance, staff awareness and well maintained, modern IT systems.
This arguably excludes advanced persistent threats, and if you are a Foreign Intelligence Services suggests ‘we can’t afford to stop you’ at this level. This is consistent with the proposed BIS Organisational Standard due to be published soon, which focuses on getting the basics right, to protect against known threats.
Aggregation
Another change to be mindful of, is the concept of aggregation does not cause an uplift in classification:
Aggregated datasets of OFFICIAL information should typically be managed within the same infrastructure and there is no threshold where increased volume will cause an uplift in the classification level, e.g. a database containing 100,000 OFFICIAL records does not become a SECRET database.
Just because a data centre holds lots of OFFICIAL data, it no longer means the aggregated set of data is now SECRET. This makes sense – this means government data centres need to be build appropriately to handle lots of OFFICIAL data, but does not make them SECRET by implication.
(But the MoD document introduces the concept of REPORTABLE OFFICIAL, which while not yet defined seem to be aggregation related).
Assurance
The picture remains far from clear on product assurance for the OFFICIAL layer. Initially the position seems to suggest products should be assured to the CESG Commercial Product Assurance (CPA) scheme, which despite its technical merits has been given a lukewarm reception by industry; industry seem to prefer alignment to the revised Common Criteria approach – something CESG has recognised and subsequently altered their stance to accept Common Criteria with some caveats. There is also uncertainty of the position of a product assured by the National Technical Authority from an EU nation state.
Just to add confusion, the MoD ISN suggests that FIPS 140-1 is acceptable assurance, contrary to the CESG view.
Inconsistency
A final worry for industry is the potential for inconsistency in the way controls are applied; it is entirely conceivable that one government department will specify a system that adopts technical standard A for the exchange of information at OFFICIAL with industry, and another technical standard B. Leaving industry with the cost of implementing two systems.
Opportunity
The above suggests an uncertain road ahead while the challenges and inconsistencies are resolved. Some are forecasting a slow-motion train wreck in progress. Is that fair?
Undoubtedly there will be issues; people will get things wrong; systems will not provide adequate protection; data will be lost. BUT I contend, this has happened and will continue to happen anyway, irrespective of the classification changed – we are already bombarded with daily stories of data loss – something has to change.
As has been discussed many times, security is a balance of people, process and technology. But traditional approaches have been technology focused, assessed by tick-box process; it is only in recently years that there has there been a people focus.
Fundamentally, the classification scheme changes are about redressing this balance, by putting greater emphasis on the people element, with personal responsibility for data in your possession – backed up by a legal framework of sanctions if the duty-of-care to protect data has been short of good-practice.
So as a challenge to the doomsday brigade, I suggest despite the rough edges identified, we should all support the change, for better or worse, it is the system we now have. Let’s use industry forums like IACG, IAAC, teckUK, UKCeB etc. to work on the rough edges and fix them. As UK citizens, it is in all of our interests to make it work – it’s OUR data after all – OUR tax records, OUR social security data, OUR nation’s intellectual property, OUR personal data, OUR nation’s security.
For more information
- Government Security Classifications video
- Cabinet Office web site
- MoD Industry Security Notice 2014/1
- Government Security Classifications FAQ Sheet 2: Managing Information Risk at OFFICIAL
- PSN community briefing
- Wikipedia

Wow, the UK Government Security Classification Scheme sounds like a real snooze fest. 😴
Are you kidding me? The UK Government Security Classification Scheme is crucial for protecting national security. It’s not supposed to entertain you like a Hollywood blockbuster. Maybe try educating yourself on the importance of these things before making ignorant comments.
“Who knew classifying government secrets could be so complicated? 🤔 #MindBlown #NeedASimplerScheme”
Oh please, it’s not rocket science. If you can’t fathom the complexity, maybe it’s time to stick to simpler topics. #NotImpressed #GrowUp
I don’t get why they have to make the classification scheme so complicated. Can’t they simplify it?
The classification scheme is intricate to accurately represent the diverse range of content. Simplifying it may compromise the system’s effectiveness. If you find it complex, try understanding its purpose and benefits before demanding oversimplification.
I mean, who comes up with these classification schemes? Feels like they just love making things complicated. #overthinking
“Wow, who knew government security classifications could be so fascinating? 🤔 #nerdlife”
“Who knew government security schemes could sound so fancy? 🤔 But seriously, do they actually work?”
Well, I’m no expert, but I guess fancy names can make anything sound important. As for their effectiveness, who knows? Governments are known for their secrets. But hey, if they’re spending our tax dollars on it, I hope it’s doing something useful.