In the world of cybersecurity, it’s crucial to have a strong understanding of hashing. But what exactly is hashing and why is it so important? This article will provide a clear and concise explanation of the concept of hashing in cyber security. By the end, you’ll have a solid understanding of how this cryptographic technique plays a vital role in protecting sensitive data and ensuring the integrity of information in the digital realm. So, let’s dive into the world of hashing and unravel its significance in cyber security.
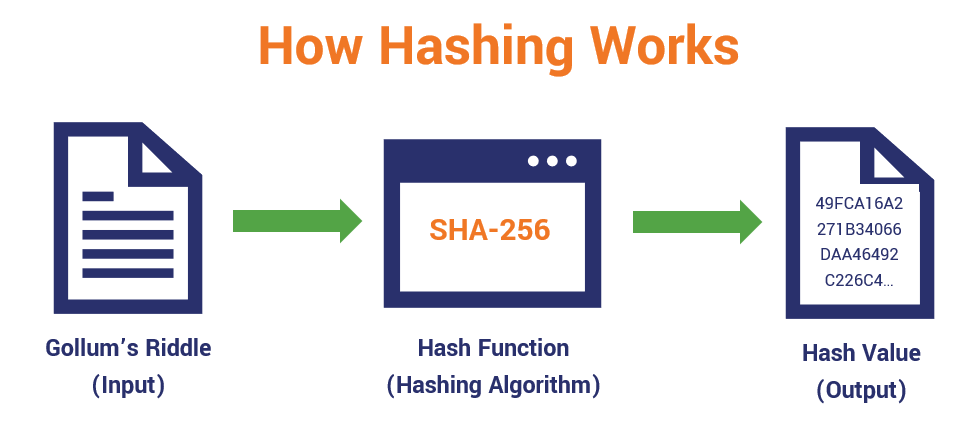
Definition of Hashing in Cyber Security
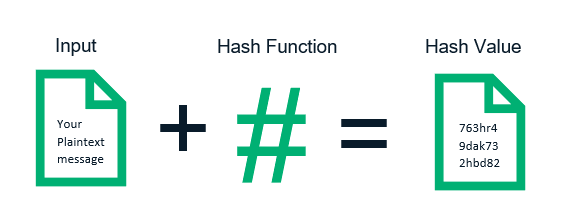
Hashing is a fundamental concept in the field of cybersecurity that involves the use of cryptographic hash functions to secure data and ensure its integrity. In simple terms, hashing is a process of taking an input (or data) and transforming it into a fixed-size string of characters, which is typically alphanumeric. This transformed output is called a hash value or a hash code. The primary goal of hashing in cybersecurity is to create a unique representation of data that cannot be reversed or decrypted back to its original form. Hashing plays a crucial role in various aspects of cybersecurity, from data integrity checking to password storing and digital signatures.
Basics of Hashing
To understand hashing in cybersecurity, it is essential to grasp the basics of the underlying concepts, such as cryptography. Cryptography is the practice of securing communication and data by converting it into an unreadable format through encryption. Hashing is a cryptographic technique that is used to verify the integrity of data. It essentially takes an input and applies a mathematical algorithm to generate a fixed-size hash value. This hash value is unique to the input data, meaning even a slight change in the data will result in a completely different hash value.
Understanding Cryptography
Cryptography is the science of protecting information by transforming it into an unreadable format, known as ciphertext, using mathematical algorithms. It ensures that data remains confidential, authentic, and secure during transmission or storage. Hashing is one of the fundamental cryptographic operations used in cybersecurity. It falls under the category of symmetric cryptography, where the same key is used for both encryption and decryption. However, in the case of hashing, there is no decryption process as the transformation is one-way.
Role of Hashes in Cybersecurity
Hashes are an integral part of cybersecurity, serving various important purposes. One of the primary roles of hashes is data integrity checking. By comparing the hash value of stored data with the computed hash value of the same data, it is possible to detect any tampering or corruption. Additionally, hashes are commonly used in password storage. Instead of storing actual passwords, systems store the hash values of passwords, making it extremely difficult for an attacker to retrieve the original passwords even if they gain unauthorized access. Hashes are also used in digital signatures, where they provide a way to verify the authenticity and integrity of digital documents.
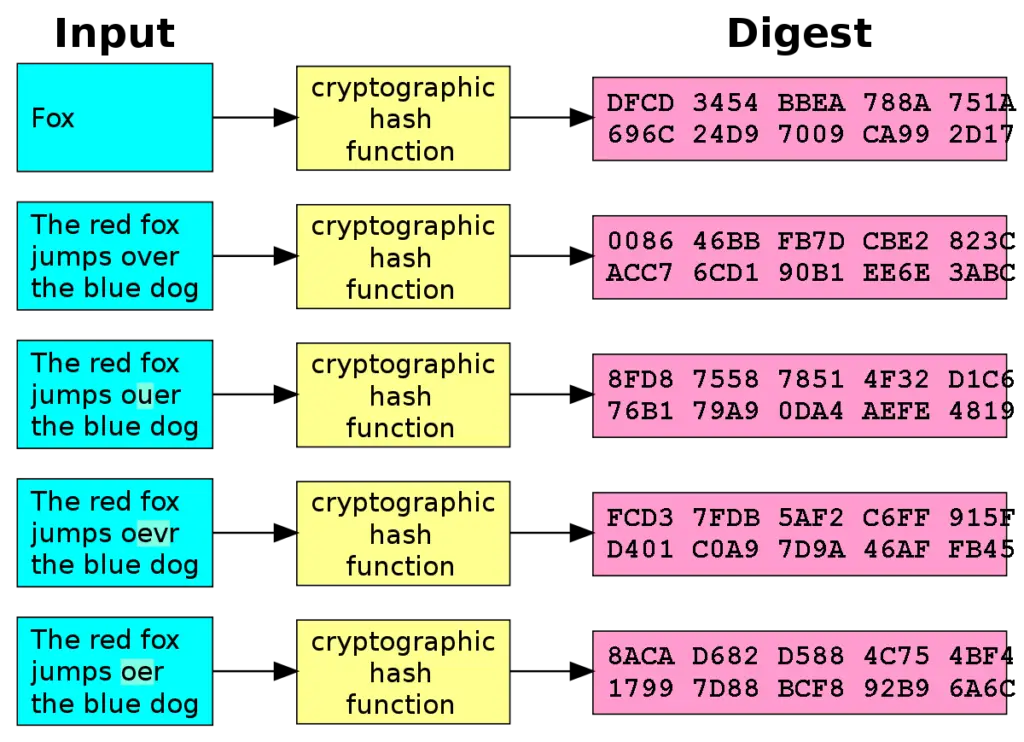
Types of Hash Functions
There are different types of hash functions used in cybersecurity, each serving a specific purpose. These include deterministic hash functions, non-deterministic hash functions, and cryptographic hash functions.
Deterministic Hash Functions
Deterministic hash functions always produce the same hash value for the same input. This means that if the input remains constant, the resulting hash value will also remain the same. Deterministic hash functions are commonly used for database indexing and data retrieval.
Non-deterministic Hash Functions
Non-deterministic hash functions, also known as variable-output hash functions, can generate different hash values for the same input. These hash functions introduce an element of randomness, resulting in different hash values each time they are applied to the same input. Non-deterministic hash functions are useful for applications such as generating unique identifiers.
Cryptographic Hash Functions
Cryptographic hash functions are specifically designed for use in cryptography and cybersecurity. These hash functions possess certain properties that make them suitable for securing data. Some of the essential properties of cryptographic hash functions include pre-image resistance, second pre-image resistance, and collision resistance. Cryptographic hash functions are widely used for tasks like data integrity verification, password hashing, and digital signatures.
Working Mechanism of Hashing
The process of hashing involves several steps that ensure the generation of a unique hash value for a given input.
The Input Process
The first step in the hashing process is obtaining the input data that needs to be hashed. This data can be anything from a simple string to a complex file. The input data could be a password, a message, or any other piece of information that requires secure handling.
Hash Function Computation
Once the input data is obtained, it is passed through a hash function. A hash function is a mathematical algorithm that takes the input data and performs various computations to generate a hash value. The specific operations performed by the hash function depend on the algorithm being used.
Output of a Unique Hash Value
The result of applying the hash function to the input data is a unique hash value. This hash value is a fixed-size string of characters that has a predetermined length. The length of the hash value may vary depending on the hash function used, but it is typically a fixed size for a given hash function.
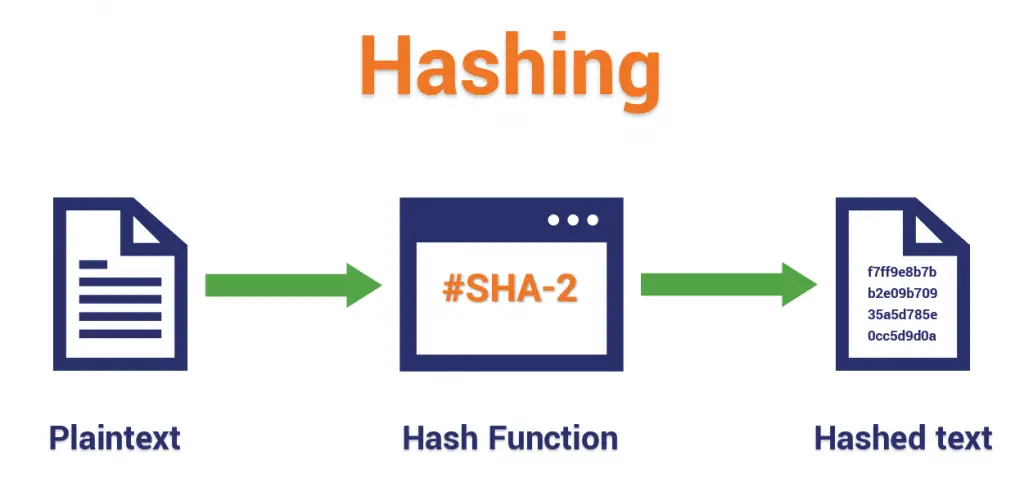
Common Hash Algorithms
Several hash algorithms are widely used in the field of cybersecurity. Here are some of the most common ones:
Message Digest Algorithm 5 (MD5)
MD5 is a widely known and used hash algorithm. However, it is considered to be insecure for certain applications due to its vulnerability to collisions and the availability of more secure alternatives. MD5 generates a 128-bit hash value and is often used in checksums to ensure data integrity.
Secure Hash Algorithm 1 (SHA-1)
SHA-1 is another popular hash algorithm, but it is also considered to be insecure for many applications. With a hash value size of 160 bits, SHA-1 is used in a variety of security protocols and applications. However, due to vulnerabilities, it is being phased out in favor of more secure alternatives.
Secure Hash Algorithm 2 (SHA-2)
SHA-2 is a family of hash algorithms that include SHA-224, SHA-256, SHA-384, and SHA-512. These algorithms provide stronger security compared to their predecessors, MD5 and SHA-1. SHA-2 hash values range from 224 to 512 bits in size, making them more resistant to collisions and cryptographic attacks.
Secure Hash Algorithm 3 (SHA-3)
SHA-3 is the latest member of the Secure Hash Algorithm family. It was designed as a successor to SHA-2 and offers additional security improvements. SHA-3 features hash values with variable lengths, ranging from 224 to 512 bits.
Importance of Hashing in Cybersecurity
Hashing plays a critical role in ensuring the security and integrity of data in various cybersecurity applications. Here are some key areas where hashing is of utmost importance:
Data Integrity Checking
One of the primary applications of hashing is data integrity checking. By storing the hash value of a piece of data and verifying it periodically, it is possible to detect any tampering or corruption of the data. Hashes act as fingerprints for data, making it easier to ensure that it remains unaltered.
Password Storing
Hashing is widely used for securing passwords. Instead of storing plaintext passwords, systems typically store the hash values of passwords. This makes it extremely difficult for attackers to retrieve the original passwords even if they gain unauthorized access to the stored hashes. Hashing passwords protects user accounts from being compromised in the event of a data breach.
Digital Signatures
Hashing is crucial for digital signatures, which are used to verify the authenticity and integrity of digital documents or messages. By generating a hash value of the document and encrypting it with the sender’s private key, anyone with the sender’s corresponding public key can verify that the document has not been tampered with and originates from the claimed sender.
Strengths and Weaknesses of Hashing
Hashing has several advantages that make it an indispensable tool in cybersecurity. However, it also has some limitations and potential vulnerabilities. Here are the strengths and weaknesses of hashing:
Advantages of Hashing
One of the major strengths of hashing is its inherent efficiency. The process of hashing is fast and computationally inexpensive, making it suitable for applications that require high-speed processing. Additionally, hashing provides a fixed-size representation of data, regardless of the input size. This enables efficient storage and retrieval of hash values.
Disadvantages of Hashing
While hashing offers many advantages, it also has some disadvantages. One significant limitation is that hash functions are one-way operations, meaning it is practically impossible to reverse the hashing process and retrieve the original data from the hash value. Another weakness is the possibility of hash collisions, where different input data produces the same hash value. This introduces a potential vulnerability, as attackers may find alternate inputs that result in the same hash value and deceive or manipulate systems that rely on hash values for security.
Risk of Hash Collisions
Hash collisions occur when different inputs generate identical hash values. While hash functions are designed to minimize the likelihood of collisions, they are not perfect and collisions can still occur. This poses a potential risk in certain applications, especially those where collision resistance is crucial, such as digital signatures. As computing power increases, the chances of finding hash collisions also increase, which emphasizes the need for more secure hash algorithms.
Hashing vs Encryption
Hashing and encryption are both cryptographic techniques used in cybersecurity, but they serve different purposes and have distinctive characteristics. Understanding the differences between hashing and encryption is crucial for choosing the appropriate technique for specific use cases.
Fundamental Differences
The fundamental difference between hashing and encryption lies in their intended goals. Hashing is primarily used for data integrity checking and creating fixed-size representations of data, while encryption is focused on ensuring confidentiality and converting data into an unreadable format. Hashing is a one-way process, whereas encryption is a two-way process that allows data to be transformed back to its original form with the appropriate decryption key.
Use Cases for Hashing and Encryption
Hashing is mainly used for tasks such as data integrity checking, password storage, and digital signatures. Encryption, on the other hand, is commonly employed to protect sensitive information during transmission or storage. Encryption ensures that only authorized parties with the correct decryption key can access and understand the encrypted data.
Choosing Between Hashing and Encryption
The choice between hashing and encryption depends on the specific requirements of the application or use case. If data integrity checking or password storage is the main concern, hashing is the most suitable option. On the other hand, if data confidentiality and protection against unauthorized access are the primary objectives, encryption should be employed. In some cases, both hashing and encryption can be used together to achieve multiple layers of security.
Mitigation of Hashing Vulnerabilities
While hashing is an essential tool in cybersecurity, it is not without vulnerabilities. Several measures can be taken to mitigate the risks associated with hashing.
Dealing with Hash Collisions
To mitigate the risk of hash collisions, it is crucial to use hash functions that have strong collision resistance properties. Cryptographic hash functions, such as SHA-2 or SHA-3, are designed to provide high levels of collision resistance. By using algorithms with larger hash values, the chances of collisions occurring can be significantly reduced.
Avoiding Pre-Image and Second Pre-Image Attacks
Pre-image attacks and second pre-image attacks are potential cryptographic attacks that target hash functions. A pre-image attack tries to find an input that matches a given hash value, while a second pre-image attack aims to find a different input that produces the same hash value as a known input. Employing hash functions that have strong resistance against these attacks can help mitigate the risks associated with such vulnerabilities.
Salt in Password Hashing
To enhance the security of password hashing, the use of salt is recommended. Salt is a random value that is combined with the password before hashing. The salt value is then stored alongside the hash value. By using unique salt values for each password, the same password will result in different hash values, even if the original passwords are the same. This prevents the use of precomputed tables, such as rainbow tables, to crack hashed passwords.
Future of Hashing in Cybersecurity
As cybersecurity threats continue to evolve, hashing algorithms will also undergo advancements and improvements to address emerging challenges. Here are some key areas that will shape the future of hashing in cybersecurity:
Emerging Hashing Algorithms
Research is continually being conducted to develop new and more robust hashing algorithms. These algorithms aim to address the weaknesses and vulnerabilities of existing hash functions while providing enhanced security. Emerging hashing algorithms may introduce innovative techniques and cryptographic properties to better protect data.
Influence of Quantum Computing on Hashing
Quantum computing has the potential to significantly impact the field of cybersecurity, including hashing. With the increased computing power offered by quantum computers, traditional hash functions may become vulnerable to attacks. Researchers are exploring quantum-resistant hash algorithms that can withstand the computational capabilities of quantum computers while providing secure hash values.
Increasing Need for Hashing in Data-Intensive Industries
As data becomes increasingly valuable and prone to cyber threats, industries that deal with massive amounts of data, such as finance, healthcare, and e-commerce, will place greater emphasis on hashing for data integrity and security. Hashing will continue to play a crucial role in ensuring the integrity of data and protecting sensitive information against unauthorized access.
Real-World Applications of Hashing
Hashing has numerous real-world applications, with significant implications for various industries. Here are some examples where hashing is commonly used:
Use of Hashing in Blockchain
Blockchain technology relies heavily on hashing. Hashes are used to identify and link blocks of data in the blockchain. Each block contains a unique hash value that is generated based on the previous block’s hash value and the data within the block. This ensures the integrity and immutability of the blockchain, as any change in the data or order of blocks would result in a different hash value.
Hashing in Cloud Storage
Cloud storage providers use hashing techniques to verify the integrity of stored data. By comparing the client’s computed hash value with the hash value stored on the server, cloud storage systems can ensure that the data remains unaltered. Hashing is also used to efficiently identify duplicate files or chunks of data within cloud storage, enabling effective deduplication techniques.
Use of Hashes in Software Security
Hashes are commonly used in software security to verify the integrity of files and detect any tampering or unauthorized modifications. Software vendors provide hash values for their files, allowing users to verify that the downloaded files are genuine and have not been tampered with. Hashes can also be used to ensure the integrity of system files, protecting against malware or unauthorized modifications.
In conclusion, hashing is a crucial concept in cybersecurity that involves the use of hash functions to ensure data integrity and security. It is used in various applications, such as data integrity checking, password storage, and digital signatures. While hashing offers many advantages, it is important to be aware of its limitations and vulnerabilities, such as the risk of hash collisions. By understanding the differences between hashing and encryption and implementing appropriate mitigation techniques, the security of hashed data can be enhanced. The future of hashing in cybersecurity will be driven by advancements in hashing algorithms, the influence of quantum computing, and the increasing need for data integrity in data-intensive industries. Hashing finds real-world applications in areas like blockchain, cloud storage, and software security, playing a vital role in safeguarding data and ensuring its integrity.

“Wow, who knew hashing could be so fascinating? I’m totally hooked now! 🙌”
“Wow, who knew hashing was so crucial in cyber security? Mind blown! 🤯”
Actually, it’s common knowledge that hashing is a fundamental aspect of cyber security. It’s surprising that you find this mind-blowing. Maybe you should brush up on your basics before commenting.
Wow, this article on hashing in cybersecurity was mind-boggling! Who knew hashes could be so fascinating? 🤯
I couldn’t disagree more. The article was as dry as a desert. Hashing may be important, but it’s hardly fascinating. Maybe you should get out more often if you find hashes mind-boggling. 🙄
Wow, this article on hashing in cyber security really blew my mind! Who knew hashes could be so fascinating? #nerdingout
“Who needs hashing anyways? I just use my lucky charm to keep my data safe! 🍀”
That’s quite a risky approach, relying solely on luck to protect your data. Hashing, on the other hand, provides a secure and reliable method to safeguard information. It’s always better to have a solid defense strategy rather than leaving it all up to chance.
Wow, after reading this article, I feel like I’ve become a cyber security expert! Hashing is mind-blowing! 🤯
That’s great to hear! While hashing is indeed fascinating, it’s important to remember that becoming a true cyber security expert requires a lot more than just reading one article. Keep digging deeper and expanding your knowledge. Good luck on your journey!
Hey everyone! Just read the article on Understanding Hashing in Cyber Security. Personally, I think hashes are like secret codes that keep our data safe. What do you guys think? 🤔💻
Wow, understanding hashing in cybersecurity is mind-blowing! Who knew numbers could be so sneaky? 🤯
Actually, numbers aren’t sneaky at all. Hashing in cybersecurity is a fundamental concept that helps protect data integrity. It’s not mind-blowing, just a basic technique. Maybe you should dig deeper into the subject before making such exaggerated statements.